In the beginning there were Google Dorks, as far back as 2002 security researchers discovered specific Google queries revealed Internet-connected devices. Seventeen years later, it is still possible to find thousands of unsecured remotely accessible security cameras and printers via simple Google searches.
Now, using search engines such as Shodan.io and Censys.io, it has become commonplace to passively discover open services (and devices) on the Internet.
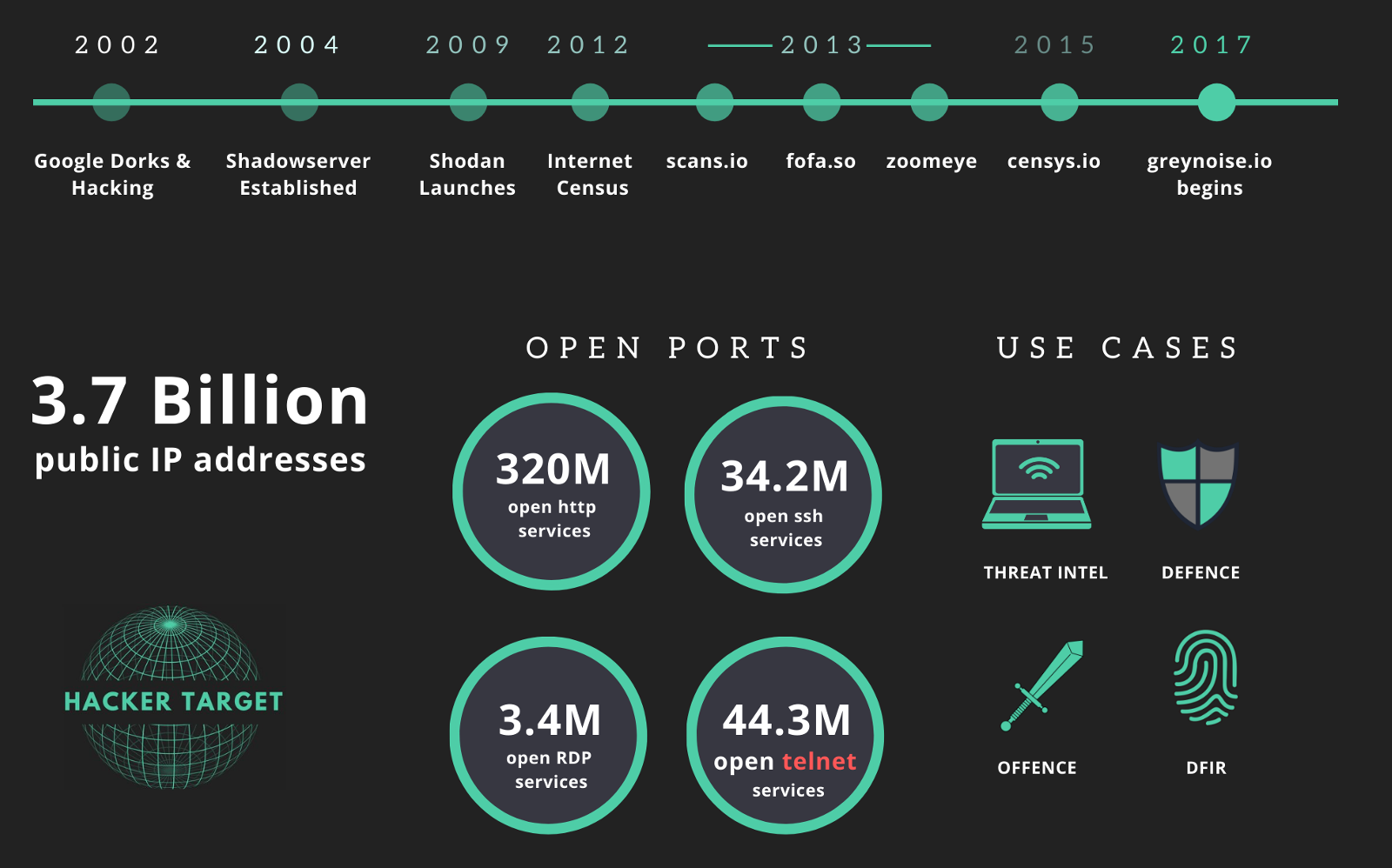
Overview of Internet Wide Scanning
The following is a brief history of Internet Wide Discovery and Scanning.
Google Dorks
Google dorks work because Google search index crawlers happened to index the admin login screen of the device. Since many devices have default credentials or no authentication at all, it is possible to view security cameras in offices around the world, print random junk to unknown printers, and much more. While pranks and much laughing may follow, Google dorks highlight the importance of security awareness. That is understanding what services are listening on your perimeter and changing default credentials.
Shadowserver
Foundeded by a group of volunteers, 2004 saw the beginning of Shadowserver. Working from the principle that sharing Internet Attack Data can only enhance the overall security of the Internet, they quickly became a primary source for security researchers. Over the years, Shadowserver has published reports, shared cyber crime data, and scanned the Internet. With a focus on cyber crime, they distribute reports of C2 services, DDOS botnet services, and other attack based infrastructure.
Shodan the Google of network services
Things started to heat up when John Matherly released the Shodan Search Tool. In 2009 John started indexing Internet service banners across the net and made the data available at ShodanHQ. It is now commonly known as the Google of network services and has made numerous appearances in mainstream media such as CNN and Forbes.
Internet Census 2012
2012 saw the release of the Internet Census. An unknown researcher created a botnet that scanned the entire IPv4 address space, then published the results online. This project was audacious and very much illegal because it utilized exploited routers to perform the port scanning.
Zmap and Masscan
Zmap was released a few months later by a team of computer scientists at the University of Michigan. The Zmap port scanning tool can scan the entire Internet in 45 minutes (IPv4 address space). You need a big fat uplink and a fast network card, but that is amazingly fast. Masscan was another extremely fast port scanner that was released only a few months after Zmap.
Project Sonar
Project Sonar was the next big project in the timeline launched by HD Moore of Metasploit fame. At Scans.io, the results of Internet scanning from HDMoore's critical.io scanning project, and data sets from the Zmap project have been made available online for researchers to explore.
Censys
Censys was created in 2015 at the University of Michigan by the security researchers who developed ZMap. A very fast port scanner capable of Internet-wide scanning. The team has been scanning the Internet and making the results available through the portal. They have recently launched commercial access to the API.
VNC pwnage
In 2013 a security researcher scanned a specific TCP port across the IPv4 address space and captured a screenshot of VNC (remote control software) services that responded with no password. In 16 minutes he found 30,000 systems with no password, and some of those systems included 2 hydroelectric plants and surveillance cameras at a casino in the Czech Republic.
ZoomEye
Launched back in 2013, ZoomEye is another online search engine for Internet connected systems. Similar to Shodan and Censys, this Chinese based service provides the ability to search by IP address or string for connected hosts that match the query. There appears to be a commercial offering also for enterprise access to scan data.
fofa.so
Another Chinese based service started in 2013 is fofa.so. This service allows searches for services, open ports, and strings across Internet Wide Scan data. Similar to other services, there is an API and the ability to perform straight string queries.
GreyNoise
A project launched in 2017 comes at Internet Wide Scanning from a different direction. GreyNoise attempts to classify incoming Internet scan traffic. Offering this classification of traffic as a service to organisations who might find this useful. The classification can highlight some of the above projects as benign, or not malicious as opposed to botnet traffic searching for more endpoints or other attack focused scanning.

Now is a good time to Scan your Internet facing Networks
It is clear from the projects, data, and articles linked above, security by obscurity was never a great strategy. Open services listening on the Internet will be found. Consequently, if they can be found, they will be attacked.
3 simple steps to help stay secure:
- Port Scan your Internet facing IP addresses with Nmap
-
- Nmap is the best tool for performing a port scan. Download Nmap and install it on your operating system of choice.
- Keep in mind to perform testing from an external IP address to the network you are testing.
- Know your network ranges. Maintain a list of all IP ranges and systems you manage. Ensure all networks and systems are tested.
- Firewall or restrict access to services that should not be Internet accessible
-
- Make the necessary changes to firewall. Block or restrict access to Internet facing devices and services.
- Implement a change control process for firewall changes and systems on the perimeter.
- Schedule the port scan to be performed on a regular basis
-
- Select a schedule based on your risk model, perhaps weekly, daily or monthly.
- Changes to the network occur all the time; when new devices are added; changes are made to existing devices; firewall rules are modified; when a change occurs mistakes will happen.
- Nmap has a tool called ndiff that allows you to compare two port scans. Ndiff is a handy tool for scripting regular port scans from a VPS or off-site location.
- 13 Vulnerability Scanners
- 17 Free DNS & Network Tools
- 4+ Billion Records of DNS / IP data
Regular port scans are simple to implement and incorporate with regular security tasks. Start now before someone on the other side of the world starts abusing your printer or turns up the heat in your building.
