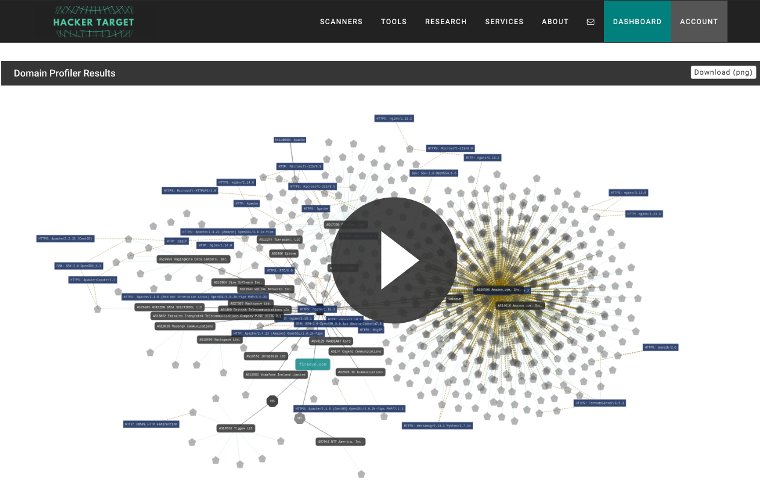
The Domain Profiler reconnaissance tool finds sub-domains and hosts for an organization. By utilizing OSINT (Open Source Intelligence Gathering) techniques we can passively discover an organizations Internet footprint.
Once you have an understanding of the IP addresses, net blocks and technology in use by an organization you can move onto the scanning and service discovery phases of an assessment.
A membership is required to use the Domain Profiler Attack Surface Discovery Tool.
Membership Benefits
Access advanced network mapping and regular scan schedules.
Discover
Discover the Internet footprint of an organization.
Identify
Find forgotten and unsecured systems.
Access Granted
To 27 Vulnerability Scanners & IP Tools.
Back-end services
Understand an organisations technology and back-end services.
Bulk Analysis
Submit lists of targets in bulk for analysis.
Passive reconnaissance
Perform competitor analysis, with passive reconnaissance.
Here are 5 use cases for the Domain Profiler Tool
- Internal Operations Team
- Check the results of this analysis against internal asset lists. Quickly find gaps in the assets or forgotten systems. Staff turnover in many organizations can lead to orphaned systems that are Internet facing and no longer maintained. Asset management systems should be aware of these systems, but sometimes they slip through the cracks.
- Incident Response
- Whether you are chasing down a major incident (DFIR) or simply in need of contextual information around a domain for alert triage. This is a tool that will surely save time during the analysis or investigative process.
- Penetration Testers
- The first stage of any penetration testing engagement is to compile open source intelligence into a picture of the target. Using OSINT methods allows a great deal of information to be collected without sending any packets to the target. This is known as passive information gathering.
- Business Intelligence
- Detailed open source information reveal technologies and third party service providers of an organizations. This can benefit a number of different investigative processes including competitive analysis. The key here is the fact that the information is from open sources, with zero impact to the target.
- Bug Bounty Hunters
- The passive nature of the information discovery, allows bug hunters (and other attackers) to quickly find systems that may be worth spending time assessing for vulnerabilities. A bounty hunter with a list of programs (domains) can submit a list of targets and watch the results come into their email box, quickly reviewing each to find easy wins.