These three enumeration techniques are a very fast way to identify users of a WordPress installation. With valid usernames effective brute force attacks can be attempted to guess the password of the user accounts.
WordPress User Enumeration via Author Archives
Finding users by iterating through the author archives is a common technique that works in all versions of WordPress by default.
Users have a unique user id that is used by the application in the database and for referencing the user account. By attempting to load the author archive for each user id, we quickly identify valid account id's and the username that matches the account. This includes the admin username (usually ID:1). This is not a new trick and is available in a number of WordPress Security Testing tools.
How does it work?
We can make a simple HTTP request to https://wordpressexample.com/?author=1. You can try this in a browser. In the web developer tools take a look at the Network tab and view the HTTP response received from the request. If it worked you will see something like this:
Connection: keep-alive Content-Type: text/html; charset=UTF-8 Date: Thu, 17 Oct 2019 23:12:26 GMT Location: https://wordpressexample.com/author/fred/ Server: nginx/1.10.3 (Ubuntu)
We can see in the response that the Location: header reveals the username for userid 1 as "fred". This indicates the admin account was renamed to "fred".
Bash One Liner - Get all the Usernames
Here is a quick bash one liner that will cycle through as many users as you want and enumerate the usernames. So if you don't have a WordPress Scanner such as WPScan or Nmap NSE scripts you can try this bash trick.
for i in {1..5}; do curl -s -L -i http://www.wordpress-site-to-test.com/?author=$i | grep -E -o "\" title=\"View all posts by [a-z0-9A-Z\-\.]*|Location:.*" | sed 's/\// /g' | cut -f 6 -d ' ' | grep -v "^$"; done
Change the 5 to however many users you want to enumerate. The command will iterate through the authors (users) and use grep to pull from the Location Header or the HTML of the actual page, depending on the sites configuration and response.
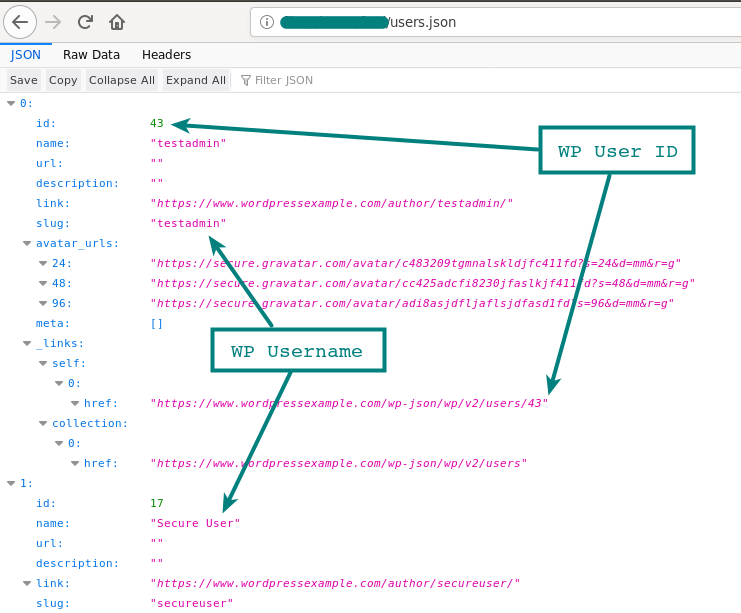
WordPress Enumeration via JSON API
Using a json endpoint it may be possible to get a list of users on the site. This was restricted in version 4.7.1 to only show a user that has published a post and if configured, before that all users were shown by default.
https://wordpressexample.com/wp-json/wp/v2/users
WordPress Enumeration via the Login Form
Brute forcing the user name is possible using the login form as the response is different for a valid vs an invalid account.
 Using a tool such as Burp Intruder in Burp Suite, we would load a list of possible usernames and cycle through HTTP POST requests to the WordPress login form examining the response.
Using a tool such as Burp Intruder in Burp Suite, we would load a list of possible usernames and cycle through HTTP POST requests to the WordPress login form examining the response.