
Contents
Introduction to Joomla Security
In 2025, Joomla continues to be a widely-used open-source content management system (CMS) with around 2.5% of all CMS-powered websites using it (approx 2 million websites globally). With the release of versions 4.x and 5.x security features have been enhanced in Joomla, including stronger password hashing, built in rate limiting for brute force protection and improved session management. But alongside this attackers develop new techniques to bypass these protections. Additionally the large ecosystem of extensions, templates and components continue to present a large attack surface.
Joomla's ease of use, free licensing, and flexible architecture, enhanced through 'extensions' much like WordPress plugins, make it a highly capable CMS. This popularity also makes Joomla a frequent target for attackers seeking to exploit vulnerable websites for malicious purposes. Many security issues stem from poor security hygiene, outdated installations, weak or reused passwords, insecure or poorly maintained extensions.
Understanding these risks are the first step in securing your Joomla site.
Enumeration and Reconnaissance
The first step in assessing a Joomla-powered site is technical reconnaissance, ie gather as much technical information as possible about how the site is configured. This information forms the foundation for identifying vulnerabilities and working out potential attack vectors.
Now is the time to put yourself in the hacker's mindset. Whether performed passively or actively, reconnaissance helps defenders understand what a real-world attacker might see. This may involve:
- Passive inspection: use standard HTTP requests to gather metadata and configuration details without interacting with the application.
- Aggressive probing: techniques such as directory brute-forcing could uncover and identify hidden components, extensions or misconfigurations. This generates noisy traffic which can be logged by web servers, detected by IDS or blocked by WAF's.
With the reconnaissance approach defined, the next step is to find out if the target is running Joomla and identify its core version.
#1 Joomla Identification & Version
To determine if the site is running Joomla, and identify the Joomla Core version, several straightforward methods can be used.
1. Meta Generator
One of the simplest ways to detect Joomla is inspecting the page's HTML source code. Look for the meta generator tag in the HEAD section.
<meta name="generator" content="Joomla! - Open Source Content Management" />
This example is taken from the source of a default Joomla install however, some site admins remove or modify this for security reasons.
2. joomla.xml
To identify the version in use, check the joomla.xml file located within the directory /administrator/manifests/files/
https://www.joomla.org/administrator/manifests/files/joomla.xml
This file typically contains version metadata such as:
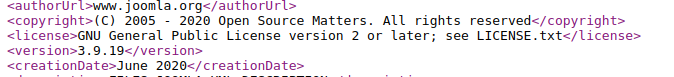
If this is accessible, this will give an accurate core version, but security admins often block access to this path.
3. Language File Disclosure
Another, sometimes overlooked source is the language XML file.
https://example.site/language/en-GB/en-GB.xml
Example entry:
<version> 3.6.5 </version>
This method can be effective even if other version indicators are hidden.
4. Version in README.txt
Check for the presence of /README.txt from the web root of the install. While it may not include the full version number, it will, usually, reveal the major release e.g. 4.x at the top of the ReadMe file which helps narrow down the attack surface.
5. Automated Detection Tools
In addition to the manual checks listed above, automated fingerprinting tools can be used to quickly identify whether a site is running Joomla and show other technologies. Using the passive options with Whatweb and Wappalyser, these tools analyse HTTP headers, file paths, and HTML signatures to detect CMS platforms and components.
Risks of an outdated installation
These version discovery techniques are commonly used by attackers. Regularly auditing your Joomla installation for exposed metadata and unprotected files is essential in reducing your security footprint.
If an attacker discovers a site running an outdated Joomla core, it may be vulnerable to known security exploit. These publicly documented exploits can often be used directly, especially if the site hasn't applied patches.
Outdated core versions can be indicative of a poorly maintained site, which can extend to other components, such as extensions, templates, and backup files. These may also be unpatched or misconfigured, which increases the likelihood of a successful attack. An unmaintained Joomla site presents a significantly expanded attack surface.
#2 Identifying Extensions and Version Enumeration
Like WordPress plugins, Joomla's functionality is extended through "Extensions", these fall into several categories:
- Modules
- Components
- Templates
- Plugins
- Languages
Each can introduce vulnerabilities when poorly coded or outdated. An common example unauthenticated users having access to the same features as logged-in (authenticated) users.
The goal of extension Enumeration is attempting to identify as many installed extensions as possible, including disabled or inactive ones. This information is valuable for discovering known vulnerabilities by checking versions against public exploit databases.
Limitations
Visibility of all installed extensions typically requires administrator access. Without this access, attackers or those testing the site can only rely on other methods, both passive and active, to enumerate extensions.
If you're looking for all extensions in a Joomla installation, you need to check multiple directories since different extension types are stored in different locations.
Passive
Hints to extensions present in a site may be found in the HTML source of the page. For example, information may appear in Javascript files, CSS files or comments on the page source. Once an extension is identified, additional details, such as version info, author, files, database tables, and installation instructions, can sometimes be gathered from the manifest file /components/com_example/manifest.xml.
Active
Some extensions do not leave traces in the HTML source. To discover installed extensions you may have to be more aggressive. Several tools can brute force Joomla paths using known extension/component names. There is no one size fits all when it comes to Joomla. Using a combination of available tools will get the best results.
One example is the Metasploit Joomla Plugin Scanner. This metasploit auxiliary module uses a wordlist to locate valid paths scanning for extensions and identify known vulnerabilities.
Vulnerability reference
Joomla maintains a live resource called - The Joomla Vulnerable Extensions List (VEL). This list tracks vulnerable extensions for which no patch is known to exist. It is strongly recommended to uninstall these extension from you site. A separate list 'Resolved Vel' includes extensions that have a patch available. Check this list and patch / update as necessary.
Extension Version Enumeration
You have compiled a list of extensions of the site, now for the version. The design of Joomla means this information isn't forthcoming or comprehensive, especially when attempting to find it passively.
It is possible version numbers can be found in an extensions manifest file or other within such as the addon's stylesheets or javascript. While inconsistent, these areas may provide enough information to help with recon.
With a valid version you can compare what has been found against known exploits or the Joomla VEL List. This comparison will attest if the site is likely vulnerable, before throwing any exploits.
#3 Template Enumeration
Joomla Templates can contain vulnerabilities that may expose the site to compromise. Templates are simply collections of PHP, HTML, CSS and JavaScript resources to define a site's design but more Complex templates have additional components and code, increasing the likelihood of security vulnerabilities.
Template Enumeration is similar to extension detection. Inspect the HTML and locate the template. Alternatively, run a passive scan on Hacker Target's Joomla Security Scan and scroll through results to find the Joomla Template.
Detecting inactive but accessible templates
One important point when testing is that Joomla Templates and components may still be installed even if they are not active. And if accessible, and vulnerable, can still be exploited. For this reason, brute-force enumeration of known template paths during an assessment is a possible additional step when assessing an unknown Joomla installation.
#4 User Enumeration
Gaining access to Joomla's administrator panel can result in the full compromise of the site. Including database access and remote code execution (RCE) via PHP. Attackers will attempt to enumerate usernames before deploying a password guessing attack.
Administrator Login Page
A quick tip is first see if the Administrator login page is publicly exposed.
https://exampledomain.com/administrator
or run a basic curl command to check if admin panel is publicly accessible:
curl -I https://exampledomain.com/administrator/
if response is
HTTP/1.1 200 OK
Then login page is exposed and publicly available. However, hardened Joomla set ups will return a 403 or redirect to main site to hide the admin panel. If accessible, this page becomes a target for brute-force or credential-stuffing attacks.
User enumeration challenges
Unlike WordPress, where simple techniques like WordPress User Enumeration can expose valid usernames, Joomla doesn't make it as easy. There are no default endpoints for listing users, and login forms do not reveal whether a username or password is incorrect.
However, most Joomla installs create a Super Administrator account with the default name of admin. As part of the install, Joomla requests a password for this account and encourages changing the name of the account from 'admin' to something more difficult to guess, but many users leave it unchanged. This makes admin a good starting point for username guessing.

Privileged User roles
Joomla defines 3 privileged user groups which have access to the control panel:
- Managers: content creation and backend system info.
- Administrators: Elevated access, admin functions excluding global options.
- Super Users/Administrator: ultimate power. Access all areas.
From version 3.2 onwards two-factor authentication (2FA) is available and can be enabled from the User Manager in the Control Panel. By enabling this, it increases login security and reduces the effectiveness of brute-force attacks.
Password Re-use and Breach Datasets
A common technique used in targeted attacks is mining public or breached datasets for credentials associated with the target. Its not uncommon for users to reuse passwords across platforms and sites. If a Joomla username is guessed or leaked, previously breached passwords can be tested. However, Joomla doesn't easily expose user lists or login info.
#5 Directory Indexing
Directory listing occurs when a a misconfigured server allows public browsing of folder contents. Instead of doing a redirect or returning a 403 Forbidden, the responds with a 200 OK and shows a list of files with the directory.
Viewing the contents of the directory allows an attacker to gather sensitive information not intended for public viewing about the existence and contents of the files. Such as hidden files, backup files, config files, plugins, and templates, without the need to brute force the paths.
How to check for directory listing
Start by browsing to Joomla-related folders and see if list of files / folders in the browser.
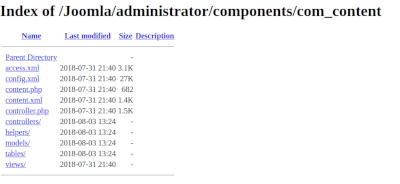
If enabled the browser returns a list of files and subdirectories. These can then be explored further.
#6 Content Discovery
Looking for sensitive information, database credentials, backups, are just a few items that can be found with content discovery using tools such as Gobuster, FFuf or Feroxbuster. Content discovery is attempting to find any interesting items contained within a web path of an application..
In 2025, many wordlists now contain CMS-specific paths, making Joomla admin areas and component directories easier to locate.
Common locations to check are:
/robot.txt
/backup
/images/
/bin/
/uploads/
/components/
/administrator/
/.htaccess.txt
/index.html
/index.php
/templates/exampletemplate
/administrator/templates/exampletemplate
/phpmyadmin/
/phpinfo.php
Gobuster example for finding hidden content:
gobuster dir -u https://example.com -w /usr/share/seclists/Discovery/Web-Content/common.txt
FFuf example:
ffuf -u https://example.com/FUZZ -w /usr/share/seclists/Discovery/Web-Content/common.txt -mc 200
Useful file examples
Backups
Files such as /backup.tar.gz or /site.zip can be accidentally left in the publicly accessible web root and can give an attacker access to all files of the installation including all installed components as well as the configuration file containing database credentials.
phpinfo()
Files like /phpinfo.php can reveal loaded modules, PHP version and configuration settings. All of which can help an attacker create or tailor exploits.
#7 Leftover Installation Scripts
Joomla's installation process creates a /installation/ directory. This directory contains scripts and files needed for the initial site set up therefore becomes a security risk if left accessible.
Joomla versions from 4.x up include protections to prevent re-running the installation file, however older Joomla installations may not have such strong protections in place and allow attacks to access the installation interaface directly.
curl -I https://example.com/installation/
#8 Joomla Scanning Tools
There are various tools for assessing and scanning Joomla installations. From passive to aggressive. Below is a breakdown of a few recon and vulnerability discovery tools.
Joomla Security Scan - Hacker Target
Hacker Target hosts a free, simple passive Joomla scan. Discover vulnerabilities, web server details, configuration errors, identify template, and test for directory indexing and others.
The freely available tools perform analysis from a simple page grab. Through the examination of the HTML source code, javascript, and a few other open publicly accessible pages, it is possible to gain an insight into the state of security on the target site. Because it performs no aggressive probing its safe to use for initial assessments.
Nuclei - Project Discovery
While not Joomla-specific, Nuclei is a fast and customisable vulnerability scanner powered by templates. In the community repo there are templates that cover Joomla version disclosure, known component vulnerabilities, admin login detection.
Here is a snippett of the joomla-detect.yaml template taken from the github repository:
nuclei-templates/http/technologies/joomla-detect.yaml
http:
- method: GET
path:
- "{{BaseURL}}/administrator/manifests/files/joomla.xml" # >= 1.6.0
- "{{BaseURL}}/language/en-GB/en-GB.xml" # >= 1.5.0 and <= 1.5.26
- "{{BaseURL}}/README.txt"
- "{{BaseURL}}/modules/custom.xml" # < 1.5.0
- "{{BaseURL}}" # >= 1.5.0 and <= 1.5.26
stop-at-first-match: true
host-redirects: true
max-redirects: 2
...
Legacy Tools Still Valuable for Joomla Reconnaissance
While several Joomla scanning tools, like those listed below, have not seen updates in a while, they remain useful in environments where Joomla is deployed in legacy or maintenance mode where updated scanners might not be applicable. These open-source tools continue to provide essential functionalities for vulnerability scanning, component enumeration, and basic fingerprinting.
- JoomScan :OWASP Joomla! Vulnerability Scanner written in Perl. Detects Joomla version, known vulnerabilities, admin login page.
- JoomlaVS: Ruby-based scanner (archived Oct 2020). Scans for components, modules, templates and basic fingerprinting.
- CMSMap: Written in Python, a scanner for Joomla, wordpress and drupal. Useful for automating scans for low-hanging fruit.
Before Moving Into Exploitation
This section outlined a number of techniques attackers use to passively and actively enumerate Joomla sites. Understanding these reconnaissance steps is vital for defenders to know what information is leaking and how attackers build their strategy. In the next section, we'll explore this information gathered and how it might be used.
Attacking and Exploitation
Securing a Joomla site requires understanding of both reconnaissance methods attackers use and the exploitation techniques that follows. This section covers exploitation tactics, including brute force attacks, vulnerabilities in extensions and core components, and misconfigurations that can lead to a sites compromise.
#9 Brute Force Joomla logins
Joomla 3.2 (2013) introduced two-factor authentication 2FA, in 2025 it still remains disabled by default. Enabling 2FA is a critical step in securing a Joomla site as attackers continue to exploit weak or default passwords.
More recent versions such as Joomla 4 and 5, have login rate-limiting and better password hashing making brute-force less effective without bypassing these protections. However, weak or reused passwords are still a risk and can be detected through various methods.
Below are a few common ways to brute-force a Joomla login page.
Nmap NSE Scripts
NMAP is most known for network discovery, however, NSE scripts extend the functionality of the popular NMAP port scanner. An Nmap NSE script is particularly helpful for performing a brute-force password against a Joomla install.
Example without a wordlist:
If you do not include a wordlist Nmap will use its default internal wordlist.
$ nmap -p 80 --script http-joomla-brute target_ip
Example with a wordlist:
$ nmap -p 80 --script http-joomla-brute --script-args userdb=/path/users.txt,passdb=/wordlists/passwordlist.txt exampletarget_ip
Burpsuite
If there is a login form on the site or you have found the administrator interface, then burp suite can be used to try to brute force the password.
There are other tools around such as JoomBrute, and others such as Hydra and Ncrack, though the latter two are most suited for other protocols.
Metasploit
Metasploit's legacy module: Joomla Bruteforce login utility works only on older Joomla installs. As you can see from the github snippet below this module attempts to authenticate to Joomla 2.5 or 3.0. It does not work against Joomla 4/5 as security has been improved for features like stronger password hashing, rate-limiting and other mitigations.
msf > use auxiliary/scanner/http/joomla_bruteforce_login
Metasploit modules are frequently added and existing modules updated. So make your Metasploit is up-to-date and look for vulnerabilities or modules relating to newer versions of Joomla.
#10 Bypass WAF
When a Joomla site is protected by a Web application Firewall (WAF) such as Sucuri or CloudFlare, some exploits or reconnaissance techniques may be blocked.
However, knowing the site's real IP address, it may be possible to bypass the WAF simply by directing traffic straight to the origin server, avoiding the DNS routing that would normally send traffic through the WAF.
Bypass via /etc/hosts
An attacker could modify their local /etc/hosts file to resolve the domain name directly to the IP:
204.0.123.23 example.com
Discovering the real IP Address
A few methods that may expose the original IP address tied to a Joomla server.
Historical DNS Records
Historical DNS record may reveal original IP address before the firewall service was implemented. Services such as DNSDumpster can reveal previous A records.
MX Records
If site hosts email on the same server as the website, records might also reveal IP addresses. Though many modern WAF/CDN setups now separate web and email hosting, which reduces this leakage.
Certificate Transparency Datasets
TLS/SSL searches against Certificate Transparency Datasets may show hostnames associated with the sites actual IP address.
