In this setup guide, we step through the process of getting OpenVAS (GVM) running on Kali 2019. Installing OpenVAS into a Kali-based system is made much easier by the inclusion of a quick setup script.
When using Kali Linux for OpenVAS scanning, resource usage should always be taken into account. Whether running Kali in a virtual machine or on bare metal, you will want to have sufficient memory and cpu available for the scanner to be optimised for speed (4 cores & 8GB should be a minimum). If you are hoping to run large numbers of parallel scans, then you will need more resources. Several performance tuning options are available in the OpenVAS scanner configuration file to better use the resources you have available. See our OpenVAS tutorial for details on modifying the configuration file.
Install
First step is to install the packages through apt install openvas.
root@kali:~# apt update root@kali:~# apt upgrade root@kali:~# apt install openvas
Config
It is then a simple matter of running the configuration script to get OpenVAS configured with required services, user accounts and the latest NVT updates from the Greenbone Community Feed.
root@kali:~# openvas-setup
The output shown here is a bit daunting, however it is all automated. Assuming all goes well you should soon have a working and up to date OpenVAS installation. The actual time taken for this script will vary depending on download speeds as it is grabbing a fair amount of data for the signatures and CVE data.
[>] Updating OpenVAS feeds
[*] [1/3] Updating: NVT
--2019-03-13 19:08:49-- http://dl.greenbone.net/community-nvt-feed-current.tar.bz2
Resolving dl.greenbone.net (dl.greenbone.net)... 89.146.224.58, 2a01:130:2000:127::d1
Connecting to dl.greenbone.net (dl.greenbone.net)|89.146.224.58|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 23071344 (22M) [application/octet-stream]
Saving to: ‘/tmp/greenbone-nvt-sync.FNJU7dvf1u/openvas-feed-2019-03-13-126973.tar.bz2’
/tmp/greenbone-nvt-sync.FNJU7dvf1u/o 100%[=============================================>] 22.00M 2.76MB/s in 9.5s
2019-03-13 19:09:00 (2.32 MB/s) - ‘/tmp/greenbone-nvt-sync.FNJU7dvf1u/openvas-feed-2019-03-13-126973.tar.bz2’ saved [23071344/23071344]
2008/
2008/secpod_ms08-054_900045.nasl
2008/secpod_goodtech_ssh_sftp_mul_bof_vuln_900166.nasl
2008/secpod_pi3web_isapi_request_dos_vuln_900402.nasl
2008/secpod_rhinosoft_serv-u_sftp_dos_vuln_900113.nasl
2008/secpod_ms08-068_900057.nasl
2008/gb_opera_file_heap_bof_vuln_win.nasl
....
[*] [2/3] Updating: Scap Data
Greenbone community feed server - http://feed.community.greenbone.net/
This service is hosted by Greenbone Networks - http://www.greenbone.net/
All transactions are logged.
If you have any questions, please use the Greenbone community portal.
See https://community.greenbone.net for details.
By using this service you agree to our terms and conditions.
Only one sync per time, otherwise the source ip will be temporarely blocked.
receiving incremental file list
./
COPYING
1,719 100% 1.64MB/s 0:00:00 (xfr#1, to-chk=41/43)
nvdcve-2.0-2002.xml
19,661,072 100% 396.63kB/s 0:00:48 (xfr#2, to-chk=40/43)
nvdcve-2.0-2003.xml
5,740,888 100% 372.54kB/s 0:00:15 (xfr#3, to-chk=39/43)
....
10,014 100% 10.57kB/s 0:00:00 (xfr#31, to-chk=2/43)
oval/5.10/org.mitre.oval/v/family/unix.xml
31,372,831 100% 395.91kB/s 0:01:17 (xfr#32, to-chk=1/43)
oval/5.10/org.mitre.oval/v/family/windows.xml
51,773,463 100% 396.37kB/s 0:02:07 (xfr#33, to-chk=0/43)
sent 3,061 bytes received 1,206,268,870 bytes 408,559.50 bytes/sec
total size is 1,205,972,114 speedup is 1.00
/usr/sbin/openvasmd
[*] [3/3] Updating: Cert Data
Greenbone community feed server - http://feed.community.greenbone.net/
This service is hosted by Greenbone Networks - http://www.greenbone.net/
All transactions are logged.
If you have any questions, please use the Greenbone community portal.
See https://community.greenbone.net for details.
By using this service you agree to our terms and conditions.
Only one sync per time, otherwise the source ip will be temporarely blocked.
receiving incremental file list
./
CB-K13.xml
1,448,830 100% 387.74kB/s 0:00:03 (xfr#1, to-chk=23/25)
CB-K14.xml
4,787,657 100% 399.75kB/s 0:00:11 (xfr#2, to-chk=22/25)
...
sha256sums.asc
819 100% 1.02kB/s 0:00:00 (xfr#23, to-chk=1/25)
timestamp
13 100% 0.02kB/s 0:00:00 (xfr#24, to-chk=0/25)
sent 614 bytes received 57,604,789 bytes 390,545.11 bytes/sec
total size is 57,589,138 speedup is 1.00
/usr/sbin/openvasmd
[>] Stopping OpenVAS services
? greenbone-security-assistant.service - Greenbone Security Assistant
Loaded: loaded (/lib/systemd/system/greenbone-security-assistant.service; disabled; vendor preset: disabled)
Active: inactive (dead)
Docs: man:gsad(8)
http://www.openvas.org/
? openvas-scanner.service - Open Vulnerability Assessment System Scanner Daemon
Loaded: loaded (/lib/systemd/system/openvas-scanner.service; disabled; vendor preset: disabled)
Active: failed (Result: signal) since Wed 2019-03-13 20:07:12 EDT; 39ms ago
Docs: man:openvassd(8)
http://www.openvas.org/
Main PID: 124044 (code=killed, signal=KILL)
Mar 13 18:53:12 kali systemd[1]: Starting Open Vulnerability Assessment System Scanner Daemon...
Mar 13 18:53:12 kali systemd[1]: Started Open Vulnerability Assessment System Scanner Daemon.
Mar 13 20:07:09 kali systemd[1]: Stopping Open Vulnerability Assessment System Scanner Daemon...
Mar 13 20:07:12 kali systemd[1]: openvas-scanner.service: Main process exited, code=killed, status=9/KILL
Mar 13 20:07:12 kali systemd[1]: openvas-scanner.service: Failed with result 'signal'.
Mar 13 20:07:12 kali systemd[1]: Stopped Open Vulnerability Assessment System Scanner Daemon.
? openvas-manager.service - Open Vulnerability Assessment System Manager Daemon
Loaded: loaded (/lib/systemd/system/openvas-manager.service; disabled; vendor preset: disabled)
Active: inactive (dead)
Docs: man:openvasmd(8)
http://www.openvas.org/
Mar 13 20:07:09 kali systemd[1]: openvas-manager.service: Main process exited, code=killed, status=15/TERM
Mar 13 20:07:09 kali systemd[1]: openvas-manager.service: Killing process 123944 (gpg-agent) with signal SIGKILL.
Mar 13 20:07:09 kali systemd[1]: openvas-manager.service: Succeeded.
Mar 13 20:07:09 kali systemd[1]: Stopped Open Vulnerability Assessment System Manager Daemon.
[>] Starting openvassd
[>] Migrating openvassd
[>] Rebuilding openvassd
[>] Stopping openvassd
[*] Please wait for the OpenVAS services to start.
[*]
[*] You might need to refresh your browser once it opens.
[*]
[*] Web UI (Greenbone Security Assistant): https://127.0.0.1:9392
? greenbone-security-assistant.service - Greenbone Security Assistant
Loaded: loaded (/lib/systemd/system/greenbone-security-assistant.service; disabled; vendor preset: disabled)
Active: active (running) since Wed 2019-03-13 20:10:10 EDT; 5s ago
Docs: man:gsad(8)
http://www.openvas.org/
Main PID: 128106 (gsad)
Tasks: 4 (limit: 14486)
Memory: 3.3M
CGroup: /system.slice/greenbone-security-assistant.service
??128106 /usr/sbin/gsad --foreground --listen=127.0.0.1 --port=9392 --mlisten=127.0.0.1 --mport=9390
??128112 /usr/sbin/gsad --foreground --listen=127.0.0.1 --port=9392 --mlisten=127.0.0.1 --mport=9390
Mar 13 20:10:10 kali systemd[1]: Started Greenbone Security Assistant.
? openvas-scanner.service - Open Vulnerability Assessment System Scanner Daemon
Loaded: loaded (/lib/systemd/system/openvas-scanner.service; disabled; vendor preset: disabled)
Active: active (running) since Wed 2019-03-13 20:10:10 EDT; 5s ago
Docs: man:openvassd(8)
http://www.openvas.org/
Process: 128105 ExecStart=/usr/sbin/openvassd --unix-socket=/var/run/openvassd.sock (code=exited, status=0/SUCCESS)
Main PID: 128109 (openvassd)
Tasks: 3 (limit: 14486)
Memory: 7.7M
CGroup: /system.slice/openvas-scanner.service
??128109 /usr/sbin/openvassd --unix-socket=/var/run/openvassd.sock
??128110 openvassd (Loading Handler)
??128111 openvassd: Reloaded 48300 of 49576 NVTs (97% / ETA: 00:00)
Mar 13 20:10:10 kali systemd[1]: Starting Open Vulnerability Assessment System Scanner Daemon...
Mar 13 20:10:10 kali systemd[1]: Started Open Vulnerability Assessment System Scanner Daemon.
? openvas-manager.service - Open Vulnerability Assessment System Manager Daemon
Loaded: loaded (/lib/systemd/system/openvas-manager.service; disabled; vendor preset: disabled)
Active: active (running) since Wed 2019-03-13 20:10:10 EDT; 5s ago
Docs: man:openvasmd(8)
http://www.openvas.org/
Process: 128107 ExecStart=/usr/sbin/openvasmd --listen=127.0.0.1 --port=9390 --database=/var/lib/openvas/mgr/tasks.db (code=exited, status=0/SUCCESS)
Main PID: 128108 (openvasmd)
Tasks: 1 (limit: 14486)
Memory: 74.4M
CGroup: /system.slice/openvas-manager.service
??128108 openvasmd
Mar 13 20:10:10 kali systemd[1]: Starting Open Vulnerability Assessment System Manager Daemon...
Mar 13 20:10:10 kali systemd[1]: Started Open Vulnerability Assessment System Manager Daemon.
[*] Opening Web UI (https://127.0.0.1:9392) in: 5... 4... 3... 2... 1...
[>] Checking for admin user
[*] Creating admin user
User created with password '450cbcd2-9999-405f-2222-951055a5e938'.
[+] Done
By utilising the prebuilt configuration script we can get up and running with OpenVAS in a very short amount of time.
OpenVAS Web Client (Green Security Assistant)
Access the Greenbone Web Client using your web browser. Login with admin and the password in the script output and you will be launching a scan of your target systems within a few minutes.
gsad
Lets first check that gsad is running and listening.
root@kali:~# netstat -apn | grep LISTEN tcp 0 0 127.0.0.1:9390 0.0.0.0:* LISTEN 128108/openvasmd tcp 0 0 127.0.0.1:80 0.0.0.0:* LISTEN 128112/gsad tcp 0 0 127.0.0.1:9392 0.0.0.0:* LISTEN 128106/gsad
Now browse to https://localhost:9392/. The Greenbone Security Assistant is a web portal front end to the GVM and OpenVAS scanner.

Task Wizard
The quickest way to fire off a scan is using the Task Wizard.
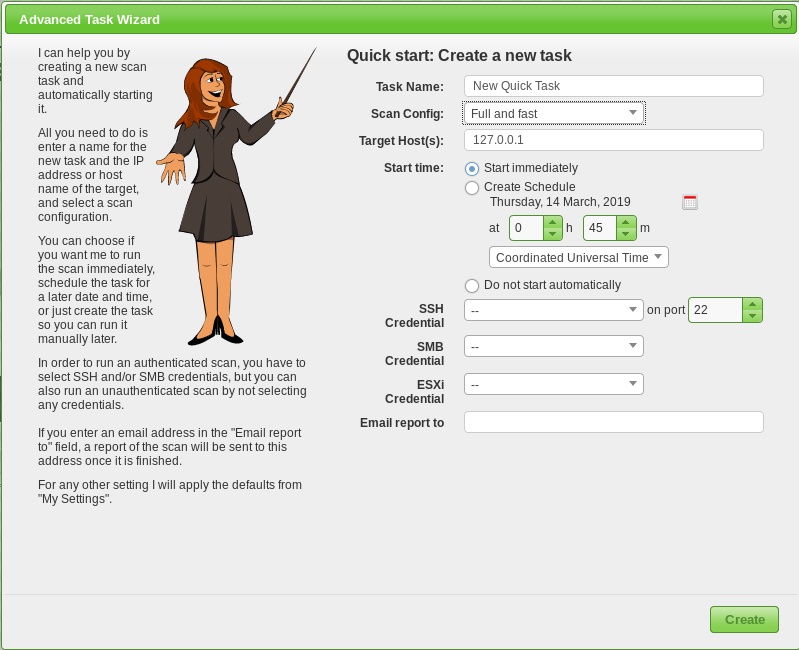
Enter the target and scan profile. Launch. Results are available under the reports option.
Modify gsad to listen on all interfaces
In the netstat output above, we can see that gsad is only listening on localhost. Here is how to change it so you can access the web interface over your local network.
Kali 2019 is using systemd for its services so we have to edit the following file to make the web interface listen on all interfaces.
root@kali:~# vi /lib/systemd/system/greenbone-security-assistant.service
Now change the 127.0.0.1 to 0.0.0.0, we also need to add a new parameter to the ExecStart line. This allows remote hosts to connect to our IP address (or hostname). Otherwise, we will get the following error in the browser:
The request contained an unknown or invalid Host header. If you are trying to access GSA via its hostname or a proxy, make sure GSA is set up to allow it.
If your IP address is 192.168.1.100 then make the changes as shown below.
[Unit] Description=Greenbone Security Assistant Documentation=man:gsad(8) http://www.openvas.org/ Wants=openvas-manager.service [Service] Type=simple PIDFile=/var/run/gsad.pid ExecStart=/usr/sbin/gsad --foreground --listen=0.0.0.0 --port=9392 --mlisten=0.0.0.0 --mport=9390 --allow-header-host 192.168.1.100 [Install] WantedBy=multi-user.target
Now restart the service and check with netstat or ss.
root@kali:~# systemctl daemon-reload root@kali:~# systemctl restart greenbone-security-assistant.service root@kali:~# netstat -anp | grep gsad tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 128654/gsad tcp 0 0 0.0.0.0:9392 0.0.0.0:* LISTEN 128653/gsad
Looks like we are up and running, now you can access the OpenVAS web interface from any system on your network.
OpenVAS Command Line Client (omp or gvm-cli)
Accessing OpenVAS from the command line is a powerful feature that gives you full control over scan tasks, reports and other management tasks. The current client in Kali is the omp client. Newer versions of GVM will use the gvm-cli command that is part of the gvm-tools package.
Both clients use XML to perform actions on the GVM server. The omp client has a number of command line switches, but the XML is where the real power lies.
root@kali:~# omp --help Usage: omp [OPTION…] - OpenVAS OMP Command Line Interface Help Options: -?, --help Show help options Application Options: -h, --host=Connect to manager on host -p, --port= Use port number -V, --version Print version. -v, --verbose Verbose messages (WARNING: may reveal passwords). --use-certs Use client certificates to authenticate. --client-cert= Client certificate. Default: /usr/var/lib/openvas/CA/clientcert.pem --client-key= Client key. Default: /usr/var/lib/openvas/private/CA/clientkey.pem --client-ca-cert= Client CA certificate. Default: /usr/var/lib/openvas/CA/cacert.pem -u, --username= OMP username -w, --password= OMP password --config-file= Configuration file for connection parameters. -P, --prompt Prompt to exit. -O, --get-omp-version Print OMP version. -n, --name= Name for create-task. -C, --create-task Create a task. -m, --comment= Comment for create-task. -c, --config= Config for create-task. -t, --target= Target for create-task. -E, --delete-report Delete one or more reports. -D, --delete-task Delete one or more tasks. -R, --get-report Get report of one task. -F, --get-report-formats Get report formats. (OMP 2.0 only) -f, --format= Format for get-report. --filter= Filter string for get-report -G, --get-tasks Get status of one, many or all tasks. -g, --get-configs Get configs. -T, --get-targets Get targets. -i, --pretty-print In combination with -X, pretty print the response. -S, --start-task Start one or more tasks. -M, --modify-task Modify a task. --ping Ping OMP server --timeout= Wait seconds for OMP ping response --file Add text in stdin as file on task. -X, --xml= XML command (e.g. " "). "-" to read from stdin. --send-file= Replace SENDFILE in xml with base64 of file. --details Enable detailed view.
OpenVAS Python Client (python-gvm)
A new feature coming with GVM is the ability to use a python client to manage the system. This is very exciting, particularly for those who like to automate all the things with Python.
Next Steps
OpenVAS (GVM) has a large number of moving parts, services, and configuration items. If you have any issues with the different services, we have an OpenVAS tutorial and guide that includes many tips for keeping an OpenVAS installation running smoothly.
Now that you have a local system ready to scan your internal network, take a look at our hosted solution where we provide the cloud infrastructure so you can check your network perimeter from the attackers' perspective.
Next Level Your Technical Network Intelligence
- 13 Vulnerability Scanners
- 17 Free DNS & Network Tools
- 4+ Billion Records of DNS / IP data
