Having yet to play with Nessus 5, today I grabbed a copy and installed it into my Ubuntu 12.04 64 bit system. Take note I am having a quick look at the product, not using it in a commercial manner as part of the work done by HackerTarget.com. This would require a professional feed license (now $1500 USD per year).
The download of the Nessus 5 package (.deb) for Ubuntu is around 25mb which contrasts significantly to the recently tested Nexpose Community Edition that weighs in at 200mb+ download for the 64 bit binary.
Install takes less than a minute and is fast and easy as can seen below.
testuser@ninkynonk:~$ sudo dpkg -i Downloads/Nessus-5.0.1-ubuntu1110_amd64.deb [sudo] password for testuser: Selecting previously unselected package nessus. (Reading database ... 193891 files and directories currently installed.) Unpacking nessus (from .../Nessus-5.0.1-ubuntu1110_amd64.deb) ... Setting up nessus (5.0.1) ... nessusd (Nessus) 5.0.1 [build R23111] for Linux (C) 1998 - 2012 Tenable Network Security, Inc. Processing the Nessus plugins... [##################################################] All plugins loaded - You can start nessusd by typing /etc/init.d/nessusd start - Then go to https://192.168.1.123:8834/ to configure your scanner Processing triggers for ureadahead ...
Heading to the URL listed in the output of the install script, starts the web based install wizard. Registering for a feed is required here whether that is for Home use or Professional use. Enter the feed key, the plugins are downloaded, and the scanner is initialised.
After setting an admin password during the web based configuration, I promptly managed to forget it. Me for the win! If you are as leet as me reset a Nessus password by running:
/opt/nessus/sbin/nessus-chpasswd admin
Nessus Management Console
After logging in you are presented with this web based console that is based on Flash. Doh! One of my least favorite things about Nessus 4 in the past has been its use of Flash, and here I see in Nessus 5 we are still using this Flash based console.
In a previous work environment where I was monitoring ~1800 devices on a globally distributed network accessing the network was reasonably restricted. If accessing from home I would use a VPN and then a Remote desktop jumpbox to access the Nessus Console on HTTPS 8834. When using the flash based console in this manner the refresh times are horrible. My connection was 20mb, the Nessus host was a grunty box, but still the slow refresh on the flash carried across the RDP redraw to make it a painful experience.
Create a Nessus Scan
Creating a test scan is easy enough. I like the clear default scan options. Lets face it; many users only use the default scan options so to clearly define the available options as "Prepare for PCI-DSS Audits", "External Network Scan", "Web App Tests" and "Internal Network Scan" helps the user understand the scope of the test.
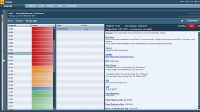
Nessus Report and Detection
The test scan did a good of detecting missing updates on my test Ubuntu host. For those unfamiliar with vulnerability scanners, I recommend you take a look at the options to customise the scan policies. Even if you are adverse to tinkering too much the most important configuration options for Internal Network Scans is to ensure you are performing credentialed scans. This allows the Nessus scanner to login to the target host machine and collect information on the host locally. Giving valuable information to the scan engine such as patch levels of the system whether it is a Windows or Linux based host.
Malware detection with Nessus
A new interesting feature of Nessus 5 is the known malware detection feature. Malware has been a problem since the days of the first boot loader virus's, however in todays world of information syphoning botnets the threats are wide spread and potentially devasting to an organisation.
Anti-virus is generally a requirement on all your Windows based desktops but it is far from fool proof. In fact slight modifications to malware can make them virtually undetectable to many AV scanners until signatures become available for that particular variant. The security industry is creating all manner of network based anomaly detection products to discover unknown malware. Tenable has added an interesting feature to Nessus that seems quite simple and one I suspect will be beneficial to many organisations.
As the Nessus scanner performs a credential based scan of a system it can collect hashes of all the running processes and compare these to an online database that is effectively a clone of a system such as VirusTotal. The system uses the Reversing Labs database of known bad hashes that can come from 25 different AV vendors. So it immediately adds a new layer of defense to your Anti-virus capability. If your primary AV client misses a piece of malware; when you run your regular Nessus scan you may still catch the unknown malware. Understand however that like any AV detection it will also not find everything. For an addon that comes free with your $1500 USD Nessus subscription I believe this is a nice bonus feature.
Summary
Overall the latest Nessus 5 seems to be light on resource usage and easy to configure. You can literally be up and running within 10 minutes. Of course this has been a very quick review, further testing would be required to see how it scales on a large network and how comprehensive the vulnerability detection plugins are.
As was mentioned in the Nexpose install review, I like to have multiple vulnerability scanner options available. It definitely helps in correlation and also provides assurance that a vulnerability that was missed by one scanner may be picked up by the second option. We feel our online OpenVAS scan and other options provide an effective second assessment option particularly when reviewing Internet facing systems.
Get more from this powerful vulnerability testing option
OpenVas Tutorial Tips and Examples
Learn more