What is Maltego?
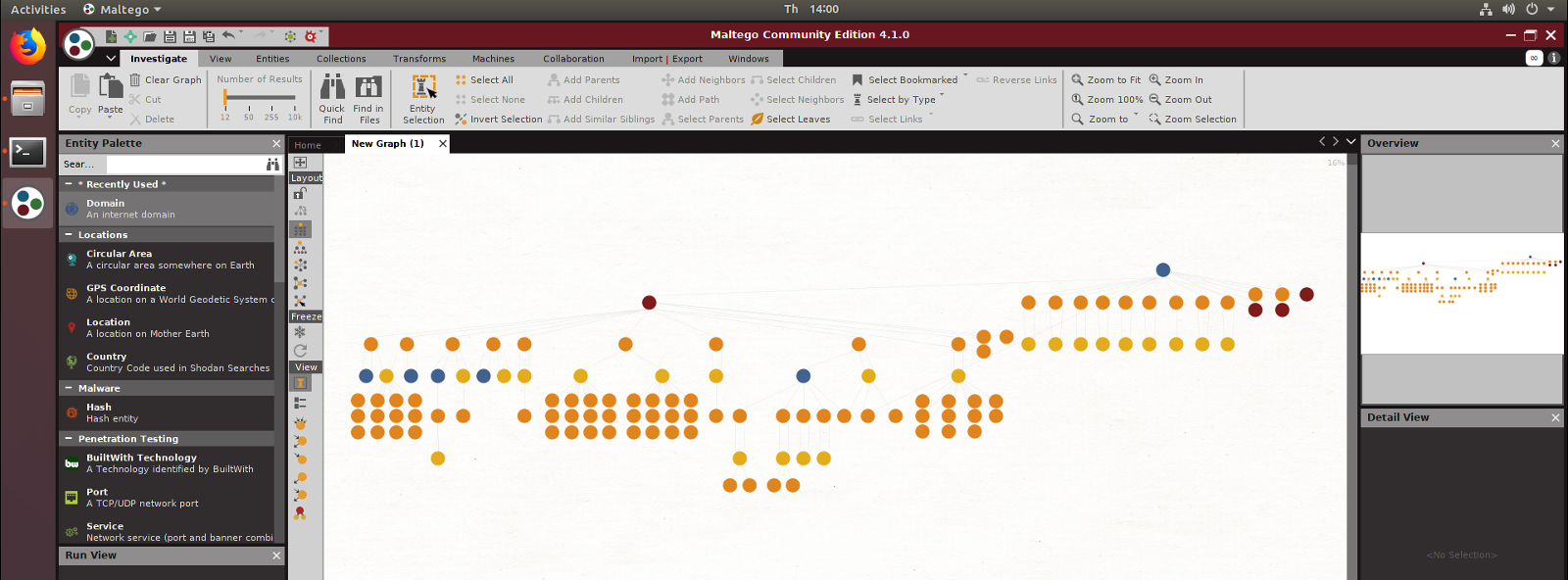
Maltego is a cross-platform application for performing link analysis. Discover relationships between entities and build a visual representation of different data with a graph based layout.
A transform is a process that pulls new data related to the entity, automatically extending the graph.
Maltego is commonly used for reconnaissance in penetration testing engagements and open source intelligence analysis (OSINT). It is possible to understand the relationship between infrastructure, services, and even users when mapping an organisations attack surface.
Using a Local Maltego Transform
There are two types of Transforms within Maltego. One runs on servers remotely, the other can run locally on the system running Maltego. Of course, as is the case with the Hacker Target Transforms, while it runs locally, the data is pulled remotely from the Hacker Target API.
Installing the Hacker Target Maltego Transforms
To run the transform, you need to have python installed along with the requests module for retrieving the data over a HTTP request. I have not tested on Windows, only on Linux, but it should work on all platforms.
The installation is straight forward. Clone (or download) the git repository. Place the files in a local directory, and add the Transforms to your Maltego installation. Either manually or by using the mtz file (Maltego Configuration File).
Head over to Hacker Target GitHub page to grab the necessary files and see the detailed installation instructions.
API Quota
With no API key set, you are limited by the number of requests you can perform each day. With a HackerTarget.com Membership, this number can be increased. If you have a membership remember to add your API key to the three transform files.
What data is available
Currently, there are three transforms available. All based on host name enumeration, for the express purpose of discovering the attack surface of a target organisation.
- GetHostNames.py - search against a domain and pull known subdomains
- GetReverseIP.py - search against an IP address and retrieve other host records pointing to that IP
- GetSharedDNS.py - search against a NS and get host records that are pointing to this NS server
This can be a circular process, as new hosts are discovered resolve these to IP address, and perform the reverse IP search. As new domains are discovered search against these with the host name search.
Sounds great but what does it looks like?
Conclusion
Maltego is a fun way to explore targets. Whether penetration testing, running down bug bounties, researching an organisation's infrastructure, or simply curious, Maltego provides a lot of value even from the community version and Hacker Target's Free API access.