Introduction
There are different versions of the NeXpose engine, we will be using the community edition on 64 bit Linux.
The company is more famous for its penetration testing framework Metasploit, so lets take a look at the NexPose engine and see how it fares against OpenVAS and Nessus.
The community edition of Nexpose is limited to 32 IP address targets. Personally, I think this is a pretty reasonable license, as it allows a small to mid-size business to gain valuable information on security vulnerabilities on their network without having to budget for a commercial product. Definitely a plus when compared to the Nessus vulnerability scanner that has a free version that is only licensed for non-commercial (home) use.
Of course, here at HackerTarget.com we are big fans of the OpenVAS vulnerability scanning suite that is open source and free to use however you like.
Download and Install
Head over to the Rapid7 site and download the version that applies to your operating system, whether you are running Windows or Linux there are binaries available for each. We have Ubuntu 12.04 on our system running 64 bit so we downloaded the file NeXposeSetup-Linux64.bin.
To start the installation process we make the binary executable and run it with sudo.
testuser@ninkynonk:~$ sudo chmod +x NeXposeSetup-Linux64.bin testuser@ninkynonk:~$ sudo ./NeXposeSetup-Linux64.bin Unpacking JRE ... Starting Installer ...
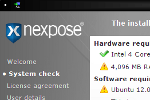
The installer does a quick check to confirm the system is suitably equipped to handle the power of the Nexpose engine. As you can see in the screenshot, the requirements are pretty decent. We initially received a warning about the package "screen" being missing, which after a quick "apt-get install screen," we were able to restart the process and get the installation underway.
Community Licence Key
It is necessary to get a community license key. A valid email address is required. The key is valid for 1 year, after which presumably you are able to get a new one.
Console and Management Access
The console and management access to the software is all over HTTPs on a web-based control panel. Login to the console over HTTPS on port 3780 (example: https://192.168.1.123:3780/).
First up is to create a site with assets. Now here I made a mistake by starting a Virtualbox guest that I was going to try scanning. My host machine has 4GB of RAM and a Core 2 Quad processor. Starting the 1GB guest proceeded to kill my system, with swap thrashing away as RAM was swapped in and out for the Guest virtualbox. Basically NeXpose needs RAM, lots of it and it will take it. I was only accessing the web interface, with no scans running, and my box was pretty much dead. Had to hit alt - f2 to grab a console and killed the VM. Eventually the system came back to normal.
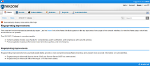
I attempted to finish the create site wizard and was presented with this error when saving.
Seems my session timed out while the disk was thrashing. Lesson learnt - use NeXpose on a dedicated host with lots of RAM. They recommend 8GB and from my experience, that is a good starting point.
Logged in again and started the create site wizard again, everything is pretty straight forward, and I moved through the options to run a scan against my local host.
Scan Results and Report
Scan of localhost took 14mins. Not unreasonable and seemed to do a good job of cataloging the installed software and discovering vulnerabilities.
Like with any vulnerability scanning tool, vulnerabilities need to be assessed to ensure they are valid, and then remediated if the risk is determined to be sufficient.
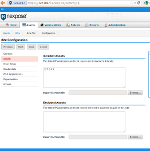
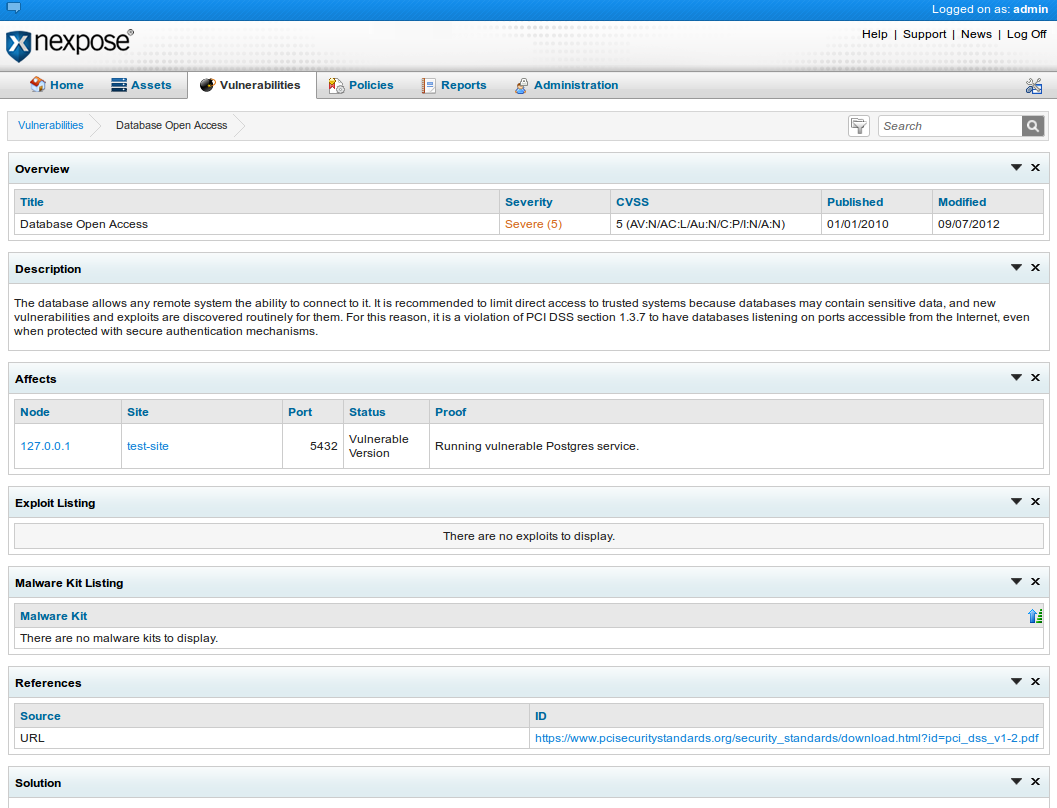
For example this screenshot shows that there is a Database vulnerability with Postgres being open to anyone. Not really. This is the NeXpose Postgres database and it is only listening on 127.0.0.1, but since this was the target IP address NeXpose thought it was open to all.
Conclusion
Overall seems like a decent product, definitely good value for small business with its free community edition. Will require some upfront costs for a dedicated system with the resources to run it. Web interface seems well laid out and has in depth risk reporting that would need to be used over time to determine how effective it might be for an organisation.
Of course for anyone using this vulnerability scanner within their organisation we would like to highlight the fact that this would complement our own hosted open source scanners. For example the online nmap port scan is a valuable tool for testing open ports on external facing systems and the OpenVAS vulnerability scanner would make a good "second opinion" to correlate with results from Nexpose.
Next Level Your Technical Network Intelligence
- 13 Vulnerability Scanners
- 17 Free DNS & Network Tools
- 4+ Billion Records of DNS / IP data