This beginner's tutorial on CyberChef will cover its core features and functions, helping you get set up and start using this powerful tool for data analysis, decoding, and more.
This easy CyberChef tutorial includes step-by-step examples and clear visuals to help you learn the basics of this Swiss-army knife tool for cybersecurity and data manipulation.
Practical examples, aimed at beginners, will walk you through tasks like extracting URLs from a file and using a built-in regex, along with tips such as how to disable operations. By the end, you'll have a solid understanding of CyberChef and how to apply it to your own work.
Getting Started: Accessing CyberChef
The images below show different ways of to access Cyberchef with the main way via Cyberchef: https://gchq.github.io/CyberChef/. You may choose to download CyberChef for local use. Downloading is optional, as CyberChef is fully functional client-side through the browser with no installation required, meaning it can be used on an ipad or android phone or anywhere you have a browser.
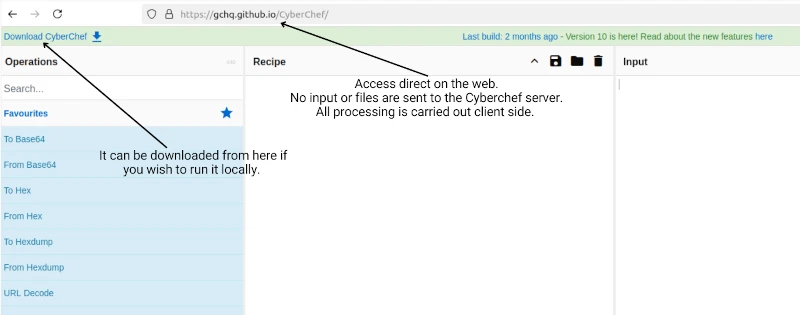
There are several reasons to consider downloading and running CyberChef locally:
- Customization: When specific custom operations are needed or modifications to the codebase are required to suit particular use cases.
- Offline Usage: For instances where CyberChef needs to be used offline and an internet connection is unavailable.
- Sensitive Data: Data is handled client side, but for an extra layer of security if handling sensitive or confidential data that should not be exposed to third parties, including ISPs or external services you may choose to run it locally.
F1 Contextual help : Useful feature
As noted on the GitHub CyberChef page, the developers introduced a help function inspired by Ghidra. While there are many options on the CyberChef screen that we can’t fully cover here, the advantage of the F1 help feature is it provides an instant reference, helping you quickly understand what each function does without needing to refer to a separate manual.
To use it, hover over an area of the screen and press F1.
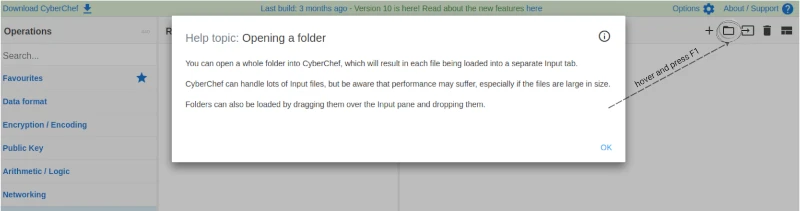
A few examples of the help content are shown in the image below, demonstrating how the F1 help feature works in Cyberchef.
How to Use CyberChef for Decoding Base64 Encoding in Vulnerability Assessments and Bug Bounty
In vulnerability assessments and bug bounty hunting, Base64 encoding can be found in places like hidden HTTP headers, hidden payloads in web applications, or even in file upload vulnerabilities. For example, an attacker might encode malicious code or shell commands in Base64 to bypass filters or detection systems.
Recognising and decoding Base64-encoded data in bug bounty hunting and vulnerability assessments can uncover hidden or obscured information that could expose security weaknesses that might otherwise go undetected.
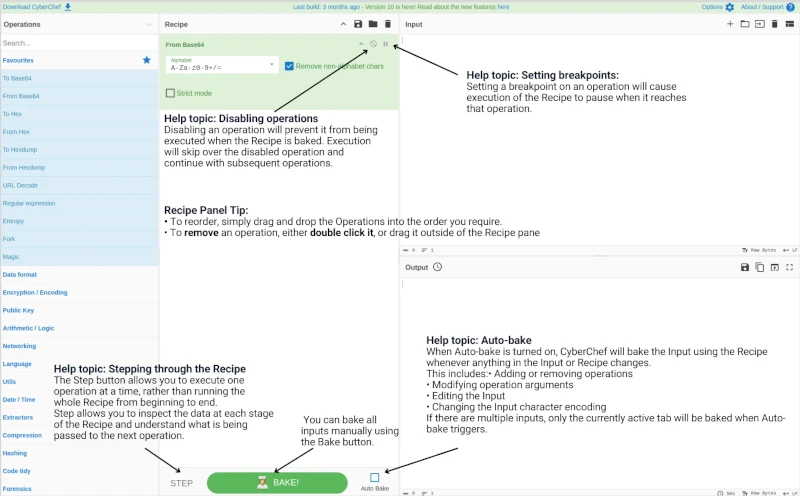
Steps to decode Base64
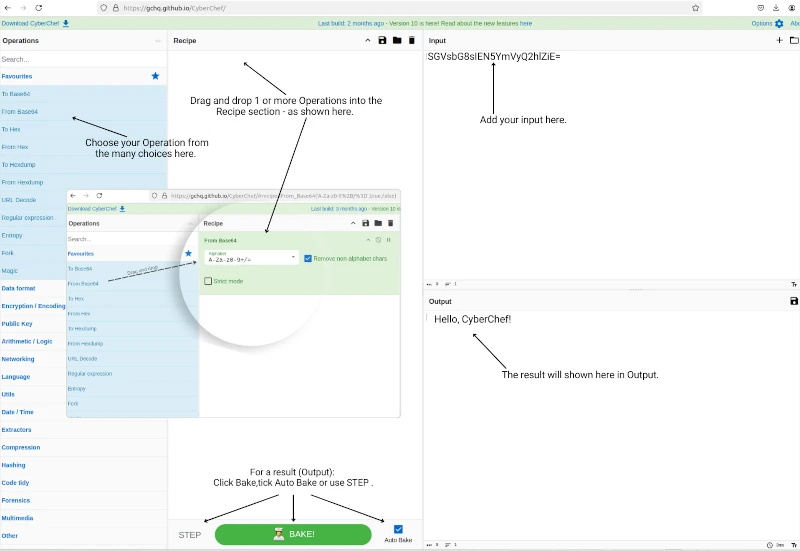
To decode Base64-encoded data using CyberChef, follow these simple steps. The order of the steps is flexible and can be adjusted based on your needs.
Locate the "From Base64" Operation:
The From Base64 operation is found under the Favorites heading in the Operations list. Click on the category heading to expand and show more available operations.
Add the Operation to Recipe:
Drag and drop (or double-click) From Base64 into Recipe section.
Input Base64 encoded string:
Paste your Base64-encoded string into the 'Input' section.
SGVsbG8sIEN5YmVyY2hlZiE=
Bake/Decode the string:
Click the green Bake button. The result appears in the Output section. Alternatively, enable Auto Bake to automatically display results without clicking Bake.
Hello, Cyberchef!
It's that simple. To clear the recipe area ready for your next bake:
Clear the Recipe Section:
To clear the Recipe section drag out, double-clicking, or use the Trash Can icon to remove all operations.
This image serves as a reference and shows areas of the interface highlighted to help you understand the process to use CyberChef to decode a Base64-encoded string.
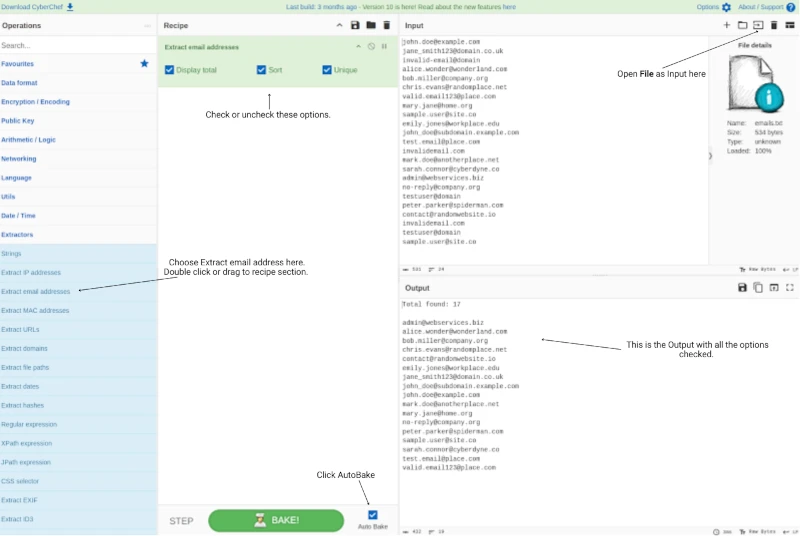
How to Extract Valid Emails from a file with CyberChef
Let’s walk through how to use CyberChef to extract valid email addresses from a file, sort them alphabetically, filter out duplicates to leave us with a list of unique addresses, and save the new list. While this can be done on the command line, we’ll demonstrate how to achieve the same result in CyberChef.
The steps are listed in a suggested order, but you can choose a different approach.
- Open the Extractors menu options.
- Locate Extract email addresses in the list.
- Double-click or drag and drop to place this operation into the Recipe section.
- Tick the options Display total, Sort and Unique.
- Click the File icon on the right side of the Input screen.
- Select your file. In this example is it a .txt file.
The contents will appear in the Input section, and if Autobake is selected, the output will appear immediately. Alternatively, click Bake each time. Have a look at the different outputs by unchecking the Unique box, or sort etc.
The following image serves as a reference and shows areas of the interface highlighted to help you understand the process.
Output Options
Using the results from the example above, here is a brief explanation of four options to manage your results.
- Saves Output to file: Save output to a file.
- Copy raw Output to Clipboard: Copy output to clipboard, making it easier to paste into another doc or application.
- Replace Input with Output: This option replaces the existing input with the current output.
- Maximise Output Window: Expands the output box to take up more space on the screen. This can make it easier to view larger or complex results.
Regular Expression (Regex) with Cyberchef
Lets explore using a simple Regex (Regular Expression) to show another way Cyber Chef can be utilised. Cyberchef includes a few built in Regex patterns. These can be used as-is to extract, modify, or verify data or they can be customised depending on the outcome you require.
It may seem like extra work when the Operation "Extract URL's" exists, and is quick and easy, however, exploring this Regex URL method provides a chance to see how regex work and allows customisation.
Regular Express Operation
Under the Operation Heading of "Extractors" find Regular Expression. Move this to Recipe section.
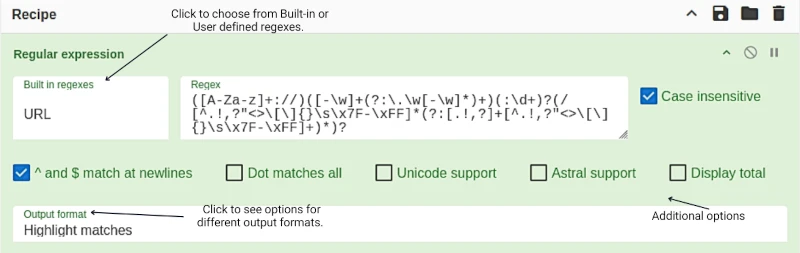
The default is "User defined" allowing you to input a regex. Click on "User defined" / "Built in regexes' to view a list of 13 built-in regexes. These are listed in the table below:
Built in Regex
IP6 address
Email Address
URL
Windows File Path
UNIX file path
UUID
Date (yyyy-mm-dd)
Date (mm/dd/yyyy)
Strings
The image above shows the Regex with the built-in URL regex selected. The corresponding regex is shown in the field next to it, and it is designed to match a wide range of URLs. Additionally, note the "Output Format" options, these allow you to choose how the results are displayed, such as highlighting matches or listing them.
Regex breakdown
Below is the full URL regex copied from the above Recipe, colourcoded with an explanation of each section.
([A-Za-z]+://)([-\w]+(?:\.\w[-\w]*)+)(:\d+)?(/[^.!,?"<>\[\]{}\s\x7F-\xFF]*(?:[.!,?]+[^.!,?"<>\[\]{}\s\x7F-\xFF]+)*)? Lets break down this regex. ([A-Za-z]+://)
Matches protocol. Eg "http", "https", "ftp", etc., followed by "://". ([-\w]+(?:\.\w[-\w]*)+)
Matches the domain part. Allows for domain names with subdomains (e.g., blog.example.com). (:\d+)?
Option for matching a port number (e.g., :8080). (/[^.!,?"<>\[\]{}\s\x7F-\xFF]*(?:[.!,?]+[^.!,?"<>\[\]{}\s\x7F-\xFF]+)*)?
Optional for matching the path, query, and fragment parts. Without matching invalid characters like punctuation, spaces, or control characters.
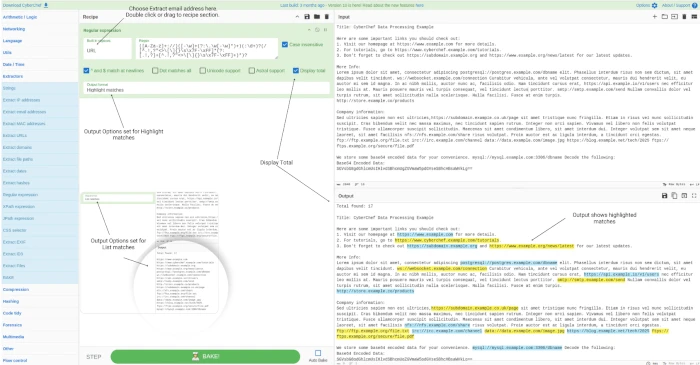
Extracting URL's from a file using a Regex
This example uses a Sample document (see below) mocked up to demonstrate how this works. It contains a mix of information buried in the text, making them hard to spot manually. The goal is to use Cyberchef to pull out the relevant parts and see what else is in there. Here is a list of things we want to do:
- Extract all URLs from various protocols.
- Place urls into a list to facilitate validation of URLs.
- Replace certain URLs with a predefined pattern (e.g., change all URLs with "example.com" to "newdomain.com").
- Decode any base64 encoded parts found.
- Save the modified document with a cleaned URL list.
File Input
Attach the file using the File Input option. This opens the document into the Input section. For your reference a copy of the sample doc is below.
- If Autobake is enabled, the document information will appear in both the Input and Output sections immediately.
- If Autobake is disabled, you can manually process the document by clicking Bake at each step as needed.
Sample Doc
With CyberChef, we can easily automate the process to extract the urls of varying protocols.
Title: CyberChef Data Processing Example
Here are some important links you should check out:
1. Visit our homepage at https://www.example.com for more details.
2. For tutorials, go to https://www.cyberchef.example.com/tutorials.
3. Don't forget to check out https://subdomain.example.org and https://www.example.org/news/latest for our latest updates.
More Info:
Lorem ipsum dolor sit amet, consectetur adipiscing postgresql://postgres.example.com/dbname elit. Phasellus interdum risus non sem dictum, sit amet dapibus velit tincidunt. ws://websocket.example.com/connection Curabitur vehicula, ante vel volutpat consectetur, mauris dui hendrerit velit, eu auctor mi sem id magna. In ac nibh mollis, auctor nunc ac, facilisis odio. Nam tincidunt cursus erat, https://api.example.io/v1/users nec efficitur leo mollis at. Mauris posuere mauris vel turpis consequat, vel tincidunt lectus porttitor. smtp://smtp.example.com/send Nullam convallis dolor vel turpis rutrum, sit amet sollicitudin nulla scelerisque. Nulla facilisi. Fusce at enim turpis.
http://store.example.co/products
Company information:
Sed ultricies sapien non est ultricies,https://subdomain.example.co.uk/page sit amet tristique nunc fringilla. Etiam in risus vel nunc sollicitudin suscipit. Cras bibendum velit nec massa maximus, nec tincidunt sapien rutrum. Integer non orci sapien. Vivamus vel libero non felis volutpat tristique. Fusce ullamcorper suscipit sollicitudin. Maecenas sit amet condimentum libero, sit amet interdum dui. Integer volutpat sem sit amet neque laoreet, sit amet facilisis nfs://nfs.example.com/share risus volutpat. Proin auctor est ac ligula interdum, a tincidunt orci egestas.
ftp://ftp.example.org/file.txt irc://irc.example.com/channel data://data.example.com/image.jpg https://blog.example.net/tech/2025 ftps://ftps.example.org/secure/file.pdf
We store some base64 encoded data for your convenience. mysql://mysql.example.com:3306/dbname Decode the following:
Base64 Encoded Data:
SGVsbG8gdGhlcmUsIHlvdSBhcmUgZGVmaW5pdGVseSBhcHBsaWVkLg==
The image below provides a visual reference for the output, including the total number of valid URLs found. In the output section, the URLs are highlighted in blue and yellow. The inset picture displays the list of valid URLs when 'List Matches' is selected in the Output Format.
Find and Replace
That covers the first two off the list of goals for this tutoral. Next is to Replace URLs with a predefined pattern (e.g., change all URLs with "example.com" to "newdomain.com").
Quick step by step:
- Search for Find/Replace or locate it under Utils in the Operations list.
- In the Find field, enter the part of the URL you want to replace, such as example.com.
- In the Replace field, enter the new value, such as newdomain.com.
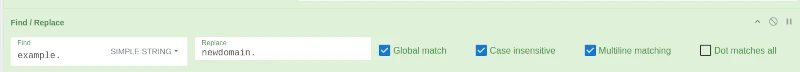
URL Find & Replace Comparison
The table above shows a sample of the 17 valid URLs that were updated using the Find and Replace method.
Find
Replace
https://www.example.com
https://www.newdomain.com
https://www.cyberchef.example.com/tutorials
https://www.cyberchef.newdomain.com/tutorials
https://subdomain.example.org
https://subdomain.newdomain.org
ws://websocket.example.com/connection
ws://websocket.newdomain.com/connection
https://api.example.io/v1/users
https://api.newdomain.io/v1/users
smtp://smtp.example.com/send
smtp://smtp.newdomain.com/send
| Find | Replace |
|---|---|
| https://www.example.com | https://www.newdomain.com |
| https://www.cyberchef.example.com/tutorials | https://www.cyberchef.newdomain.com/tutorials |
| https://subdomain.example.org | https://subdomain.newdomain.org |
| ws://websocket.example.com/connection | ws://websocket.newdomain.com/connection |
| https://api.example.io/v1/users | https://api.newdomain.io/v1/users |
| smtp://smtp.example.com/send | smtp://smtp.newdomain.com/send |
Disable Operation
Save document
The last step in the process is to save the the doc to a file. Straight forward and covered in the tutorial under "output options".
Advanced Cyberchef technique
Looking for some serious advanced cyberchefs techniques - check out Embee Research's you tube:
Conclusion
If you are are interested in learning a bit more on the history of cyberchef and how it came to be released as open source read: How GCHQ made its cyberchef app open source .
In this Cyberchef tutorial, we've walked through a series of steps to process and clean a document using CyberChef. We also covered the icons and operations available, helping you to understand their purpose and how to use them.
Throughout the tutorial, the examples were designed to highlight how CyberChef can simplify and streamline tasks, making complex operations accessible for beginners.