The Vulnerability Scanner
A vulnerability scanner identifies exposed services, outdated software, and insecure configurations across networks and web applications; helping uncover security weaknesses missed during deployment and ongoing operations.
What is a Vulnerability Scanner?
A vulnerability scanner is software that identifies weaknesses across networks, systems, and web applications. Although the concept may seem straightforward, the process itself is more complex.
For most organisations, having a thorough understanding of assets and conducting regular vulnerability scanning is the most cost-effective approach to getting security under control and prevent avoidable incidents.
Once vulnerabilities are detected, it's time to evaluate and assess the risk. This allows you to priortise and work on mitigation.
Despite growing investment in threat intelligence, analytics, and offensive security programs, vulnerability scanning remains the foundation of effective defence. Without clear visibility into exposure and attack surface, advanced tools quickly become noise rather than protection.
– Center for Internet Security Control 4: Continuous Vulnerability Assessment and Remediation

The Assessment Cycle
A vulnerability scanner is the tool that enables the vulnerability assessment process. There is no start and end to the security assessment process it is an ongoing effort.
Software undergoes daily discovery of new vulnerabilities, while networks constantly evolve. These two facts underscore the necessity for a continuous process essential.
What Can a Vulnerability Scanner Detect?
Due to the broad range of vulnerabilities that need to be assessed there are a wide range of different tools to perform different types of testing.
What can a vulnerability scanner detect?
- Known Software Vulnerabilities (unpatched or unsupported software)
- Insecure Configuration within Networks and Systems (poor default security or user error)
- Default or Weak Passwords (a top access vector for attackers)
- Web Application Vulnerabilities such as SQL injection (SQLi) and Cross Site Scripting (XSS)
- Information Leaks (revealing too much configuration or other information can open doors for attackers)
With the wide range of types of vulnerabilities, there are a range of tools that can be used to detect these different vulnerability types.
Web Application Vulnerability Scanners
Web application scanning involves looking for insecure code that introduces vulnerabilities such as those from the OWASP Top 10. These vulnerabilities such as SQL Injection and Cross Site Script are not always in packaged software. Other than commercial applications these types of vulnerabilities can also be found in open source software and internally developed applications.
These types of scanners range from intercepting proxies such as the popular Burp Suite to the focused SQLmap a highly accurate SQL Injection testing tool. Enterprise level tools such as HCL Appscan also exist that spider an application searching for vulnerabilities. These tools are often used internally by large web application development teams as part of the secure software development life cycle (SDLC).
Network Vulnerability Scanners (Internal & External Scanning)
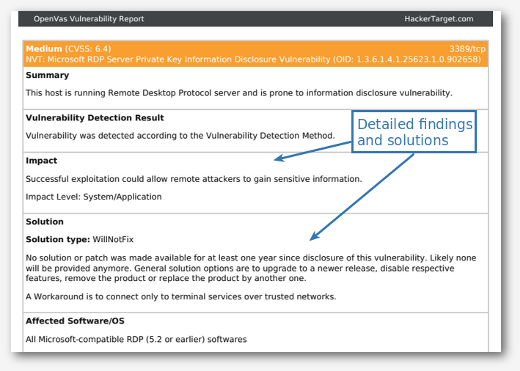
A network vulnerability scanner can go very wide but will not necessarily go deep on all vulnerability types. With these types of scanners you can have a database of over 50'000 known vulnerabilities. These will attempt to detect old server versions that have known vulnerabilities, check for default credentials and scan for known scripts. A good example of a network vulnerability scanner is the open source OpenVAS system. We use this open source tool in our suite of hosted online vulnerability scanners. Other well known examples include the commercial Nessus, and NexPose from Rapid7.
A different example of a Network Vulnerability Scanner is the Nmap Port Scanner. This tool does not go as broad in its detection, but it is more focused on mapping open ports (services) across a network. An open port that should not be accessible can still be a vulnerability.
Running a network vulnerability scanner within your network is a useful way to understand how well systems management is undertaken within the organisation. Ideally, these types of Internal scans are conducted using a credentialed scan. The scanner has valid credentials and can log onto the systems it is testing to accurately assess whether known vulnerabilities within the software and operating system have been patched.
External vulnerability scans are often conducted from outside the network perimeter and assess the external exposure of the network. That is a picture of the network from an external attacker's point of view. These types of external scans are often used to complement Internal testing. Using a different vulnerability scanner for the Internal and External scanning is generally best practice as it ensures you get the best coverage of vulnerabilities. No vulnerability scanner is perfect as it all comes down to the database of checks and the ability for the scanner to accurately match the checks with the identified attack surface.
False positives are common with most vulnerability scanners, and they can take time to confirm, but a false negative is worse. In this case, rather than detecting a vulnerability that is not present, the scanner fails to identify an actual vulnerability. By using multiple tools you are better able to avoid missing the false negative.
Attack Surface Discovery
A key to keeping your vulnerability exposure under control is to have an accurate asset register. In theory, this should detail all the endpoints, services, and web sites. However, this is rarely the case even in an organisation with a mature security practice. An attack surface discovery process emulates the attacker and can identify gaps in the asset register.
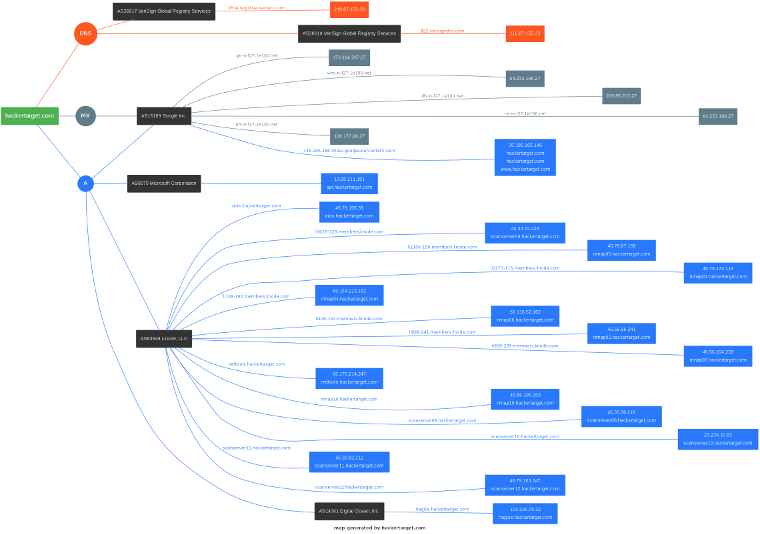
Domain Profiler Example Result
Recently several tools have become available that go deep into the process of Attack Surface Discovery.
When presented with a target organisation, an attacker will want to discover as much about the target infrastructure as possible.
Using open source intelligence resources, as well as non-intrusive or passive reconnaissance techniques the attacker can quickly identify endpoints and web sites that belong to the target.
It is then a matter of mapping the attack surface and looking for vulnerabilities. This mapping moves from passive to active discovery with packets sent to the target network. Port scanning and visiting web sites to determine web applications in use are two examples of the mapping process.
The image shows a map of a target domain that was generated using the Domain Profiler tool. It works by querying large DNS datasets and other open source information to develop an attack surface mapping of a target domain.
Focused / Specialist Scanners
Outside of the broad categories outlined above are a large number of more focused tools. A few examples of these are tools such as Nikto (web server and site scanner), WPScan (a WordPress testing tool), Aircrack-NG (wireless network testing) or one of the hundreds of tools included in the Kali Linux distribution.
Smaller, specialized tools have the advantage of probing specific vulnerability types in greater depth. They also streamline understanding of the testing process, making manual testing and verification an easier process.
Choosing the Right Vulnerability Scanner
Your scanner found 10,000 vulnerabilities. Which 10 do you fix first? A great scanner helps you separate the background noise from the critical exploits that attackers are using.
| Scanner Category | Focus Area | Ideal Use Case | Key Capabilities | Key Tools |
|---|---|---|---|---|
| Network / Infrastructure | IPs, Ports, Services | Internal/External Sanity Checks | Missing patches, weak SSH/SMB configs, rogue services | OpenVAS, Nessus, Nmap |
| Web Application (DAST) | Running Apps & APIs | Testing Web Front-ends | OWASP Top 10, SQLi, XSS, Broken Authentication | Burp Suite, Nikto, OWASP ZAP |
| Static Analysis (SAST) | Source Code | Source Code Review | Hardcoded secrets, insecure functions, logic flaws | SonarQube, Snyk, Semgrep |
| Attack Surface (ASRM) | Unknown Assets | Shadow IT Discovery | Subdomain enumeration, DNS hygiene | HackerTarget Domain Profiler |
| CMS-Specific | WordPress, Joomla, Drupal | Content Management Systems | Plugin/theme vulns, outdated core, weak admin panels | WordPress Security Scan, Joomla Security Scan, Drupal Security Scan |
What a Modern Scanner Must Detect
- Critical CVEs: Immediate identification of high-reach vulnerabilities.
- Misconfigurations: Open S3 buckets, default admin credentials, and exposed `.git` directories.
- Information Leaks: Server headers, verbose error messages, and internal IP disclosure.
- End-of-Life (EOL): Detecting software no longer receiving security updates.
What about Penetration Testing?
Everyone knows about Penetration Testing, it is exciting and involves hiring people in dark hoodies .
Well not really. A penetration test is a simulated attack with the goal of actually breaking into a system, often with a goal or trophy to prove the access. The focus of the test is to gain access rather than find all the vulnerabilities across the attack surface.
For most organisations, penetration testing should not even be considered until the vulnerability assessment and remediation process is active and has had time to work. Once you have a handle on the vulnerabilities now is the time to think about Penetration Testing and the budget that goes with it. A penetration test is expensive, usually costing tens of thousands of dollars. Without an understanding of your vulnerability exposure you are wasting your money.
Finding the Low Hanging Fruit
Being an automated test, the vulnerability scanner isn't flawless. However, it effectively pinpoints low-hanging fruit, making it a valuable tool in security assessments.
Whether it's simple configuration errors, default passwords, or systems that missed the latest patch, attackers target the low-hanging fruit. After all, if simplicity can get you through the door, why waste time on more sophisticated attacks?
Before having a Penetration Test performed, check the attack surface with vulnerability scanners. Remediate any issues found and make the penetration testers use more sophisticated attacks - in other words get your money's worth.

We love the service and would like to upgrade our plan.
– John T. Security Analyst
About our Hosted Tools
At Hacker Target, we host trusted open source security tools. This has a several benefits; a primary one being simplicity. There is nothing to install or maintain, all the software is hosted on our remote servers. Tools can be tested against your infrastructure and web sites in a couple of clicks. This makes it an excellent solution for small security teams, as well as a great tool kit for larger more mature security practices that can complement existing solutions.
In addition to the selection of vulnerability scanners, we also have Free access to a number of DNS / IP Tools. These resources serve for troubleshooting, conducting research, and gathering information throughout security assessments.
Knowing what services are running on your systems, and being able to identify if and when any of those services change, is the first step in securing your network.

| Scanner | Description |
|---|---|
| Nmap Online Port Scanner | Open ports are checked with the leading port scanning tool Nmap. A great tool to test firewall for open ports and services. Identification of services is performed through banner checks and other methods. |
| OpenVas Vulnerability Scanner | Open network services are scanned and then analyzed for security vulnerabilities. The tool is plugin based with a database of over 20'000 known vulnerabilities. Reporting options include native html or an enhanced PDF option. |
| Nikto Web Server Scan | Nikto tests web servers for vulnerable configurations, scripts that have security issues and other known problems. |
| WhatWeb Web Site Analysis | Discover installed web technologies from an examination of the html code. Reveals content management systems, javascript frameworks, web servers, server side scripting, geolocation and more. |
| Drupal Security Scan | Test Drupal Installation Security from an external perspective through a handful of simple web requests. Checks for basic security misconfiguration, analysis of links and other security problems can be found with this non-intrusive tool. |
| Joomla Security Scan | Test Joomla Installation Security from an external perspective; both passive (non-intrusive) and active scanning modes. The active scan utilises the Joomscan open source tool to perform a deeper security audit of a Joomla installation. Similar to the WordPress Security Test. |
| WordPress Security Scan | Test WordPress Security from an external perspective, use the passive scan option quickly assess a wordpress site and gather information. The active scan using the WPscan tool performs a more in depth check of plugins and other vulnerabilities. Information is compiled and placed into an easy read report with recommended security fixes and improvements. |
| Domain Profiler | Attack Surface Discovery is a primary objective when assessing an organsiation from the attackers perspective. Find external facing assets, networks and systems through analysis of open source intelligence. The Domain Profiler tool performs an initial overview of an organisation using a domain as the initial seed. |
28 Tools and Vulnerability Scanners
7-day money-back guarantee. No questions asked.