Use this automated version of the hosted Nmap Port Scanner to monitor your Internet facing systems, and be alerted to changes on your servers, firewall or border routers.
Port scans can be scheduled to run on a recurring basis daily or weekly depending on your requirements.
Get alerted to changes in Internet facing systems and networks
Membership Benefits
Access advanced network mapping and regular scan schedules.
Monitor Changes
To firewalls and network perimeters
Schedule daily scans
Be alerted on changes.
Access Granted
27 Vulnerability Scanners & IP Tools.
Tactical Reports
Correlate with Firewall Change Control.
Discover New Services
Backdoor, or simply #YOLO devops?
Email Alerts
Detected port changes
Additional Information
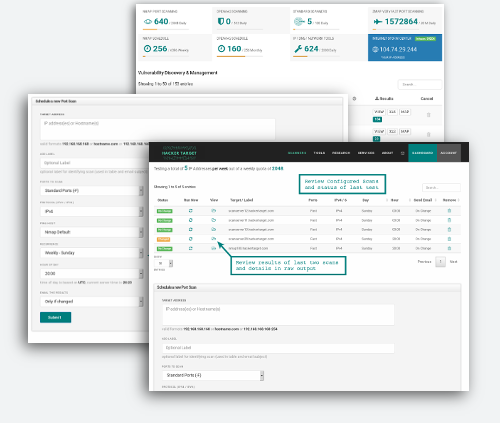
Selecting Your Targets
With this automated Port Scan, you can scan an single IP address 192.123.x.x, a hostname scanme.nmap.org or a range of IP addresses 192.168.0.0/24. It is also possible to schedule a list of targets in one hit using the bulk add option as noted below.
If you wish to target a range of IP addresses you may use the format 192.168.1.1-50 or in CIDR 192.168.1.0/24. This can be up to a full /24 net block. 254 IP addresses are the maximum amount that can be scanned on one scan profile.
Target Selection - Ensure any network ranges do not overlap onto targets you do not have permission to scan.
Adding targets in bulk
Multiple targets can be added by submitting a list of targets. All targets from list will have scan properties as selected in the form. It is not possible to add both IPv4 and IPv6 targets as a list (create two lists). Note that adding multiple targets with different labels is possible by having the list contain comma separated values.
Example csv for adding a list of targets
192.168.1.1,target1-label
192.168.1.2,target2-label
192.168.1.3
192.168.1.4,target4-label
Determining the number of available Scans
The number of IP addresses that can be scanned is based on a weekly quota. If you scan a full Class C net block every day, this is adds up to 7 x 254 = 1778 weekly count. Alternatively you could scan 4 x Class C once per week and still stay under a weekly quota of 2000 per week.
Time of Scheduled Scans
The scans can be scheduled for any hour during the day. Port scans are then queued on that hour, and will run in sequence. If you scheduled 20 scans for 13:00 UTC they will not all run simultaneously right on 13:00, they will be queued at 13:00 and run as scan servers are available.
Viewing Results and Status
The status is determined by comparing two most recent Nmap scans. The scans can be initiated manually through the web interface or launched as part of a scheduled scan operation. The comparison of the results is simply the result of using the Nmap tool ndiff and determining if there is a difference in the responding hosts as well as the port and service results.
| No Change | This indicates the previous two scans are identical. |
| Changed | This indicates there is a difference in results of the previous two scans. |
| No Data | There is not enough data to determine the status (results not available for comparison). |
| Running | An Nmap scan is currently running, progress will be indicated in the table above. |
| Queued | The scan is currently queued to run when the next available server is available. |
| Error | There was a problem running the scan, try again or contact support if this continues |
Email Alerts
Results are delivered to the user in an email, depending on the user selected email option in the scan profile.
- Results after every scan: If a user chooses to receive results every time then an email is dispatched following the completion of the scan
- If change detected (default): Emails are only sent if a change is detected in the scan results. This could be a change in
open / closed / filtered ports or if a host is no longer responding to Nmap's host detection.
- If open ports change: Depending on the target network and other factors some clients find that they get a number of false positives in closed vs filtered ports. To minimise alerts on false positives this option only sends an email if the change is detected in the
open ports on the target network or host.
All results are able to be accessed through the web interface.
Load balanced hosts or hostnames that resolve to multiple IP addresses
Hostnames that resolve to multiple IP address are scanned across each of the IP addresses. This ensures that alerts are only generated on changes on any of the resolved IP addresses. Uses the nmap option --resolve-all that was introduced in Nmap 7.70.
Understanding "0 hosts UP"?
If you are testing open ports daily or weekly and find Nmap is returning 0 hosts up. There are a few possibilities. If your external facing system is not responding to Ping from external sources then the IP Address will not be scanned. Nmap first attempts to discover if your system is UP by sending an ICMP ping; so in the event that your border firewall or router is dropping ICMP packets the scanning will not continue as your systems will be classed as being down.
A second thing to check is that you have specified the correct protocol IPv4 or IPv6 depending on your system. A system wrongly classified will be reported as being down, as the Nmap scanning engine will not receive a Ping response from the invalid IP Address.
Intrusion Prevention Systems are also a possible cause of the lack of response, if you are using a system with a IPS in place. The IPS may detect the scan and block packets from our IP Address. Check your IPS for alerts or if you are a hosted customer check with your service provider to see if they have any IPS blocking mechanisms in place.
Skipping host x.x.x.x due to host timeout
In the results you may encounter host timeout errors from Nmap. This indicates that the scan of that particular host did not complete within the maximum timeout, which is set to 90 minutes. It is unusual for this to occur under normal conditions. We do sometimes see it happen on target networks that are slow, or networks that have Intrusion Prevention Systems in place that detect the incoming port scan and throttle the traffic significantly slowing down the scan.
If you continue to receive these messages, and are confident your local network is not causing the delays in the port scan, contact support and we will investigate from this end.