Running a Nikto web server scan is a straight forward process. Follow through this Nikto Tutorial to get an overview of what is involved. Start your web server testing with one of the most well known website / server testing tools. This is the same tool we use in our hosted Nikto scanner service.
Nikto is a perl based security testing tool and this means it will run on most operating systems with the necessary Perl interpreter installed. We will guide you through using it on Ubuntu Linux, basically because it is our operating system of choice and it just works. Perl comes already installed in Ubuntu. So it is a matter of downloading the tool, unpacking it and running the command with the necessary options. For Windows users running Nikto will involve installing a perl environment (activestate perl) or loading up a Linux virtual machine using Virtualbox or VMware.

If you are running Microsoft Windows as your main operating system you may find having a virtual machine with Kali Linux or Ubuntu will bring a number of benefits. For a starters it makes getting tools such as Nikto a very simple process, as well as develop some skills using Linux based operating system that will benefit all aspects of your security testing. The majority of free security testing tools are developed on and for Linux based systems. By using a virtual machine you can test Nikto and many other open source security tools without affecting your production workstation.
Nikto Installation on Ubuntu
On a default installation of Ubuntu, launch a terminal and using a standard user account download the latest version of Nikto.
test@ubuntu:~$ wget https://github.com/sullo/nikto/archive/master.zip
You can unpack it with an archive manager tool or use tar and gzip together with this command.
test@ubuntu:~$ unzip master.zip test@ubuntu:~$ cd nikto-master/program test@ubuntu:~/nikto-master/program$ perl nikto.pl
You should see the following output after running nikto.plThis should be your results from a working installation:
test@ubuntu:~/nikto-master/program$ perl nikto.pl
- Nikto v2.1.6
---------------------------------------------------------------------------
+ ERROR: No host or URL specified
-config+ Use this config file
-Display+ Turn on/off display outputs
-dbcheck check database and other key files for syntax errors
-Format+ save file (-o) format
-Help Extended help information
-host+ target host/URL
-id+ Host authentication to use, format is id:pass or id:pass:realm
-list-plugins List all available plugins
-output+ Write output to this file
-nossl Disables using SSL
-no404 Disables 404 checks
-Plugins+ List of plugins to run (default: ALL)
-port+ Port to use (default 80)
-root+ Prepend root value to all requests, format is /directory
-ssl Force ssl mode on port
-Tuning+ Scan tuning
-timeout+ Timeout for requests (default 10 seconds)
-update Update databases and plugins from CIRT.net
-Version Print plugin and database versions
-vhost+ Virtual host (for Host header)
+ requires a value
Note: This is the short help output. Use -H for full help text.
If there are any errors regarding SSL support it may be necessary to apt install libnet-ssleay-perl. Without SSL/TLS support you will not be able to test sites over HTTPS.
Starting a Nikto Web Scan
For a simple test we will use test a single host name. In the example below we are testing the virtual host (nikto-test.com) on 16x.2xx.2xx.1xx over HTTPS. The web server on the target responds to the Nikto tests as it would any request to the web server, we can see from the results that the target is a WordPress based site.
test@ubuntu:~/nikto-master/program$ perl nikto.pl -host https://nikto-test.com
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 16x.2xx.2xx.1xx
+ Target Hostname: nikto-test.com
+ Target Port: 443
---------------------------------------------------------------------------
+ SSL Info: Subject: /CN=nikto-test.com
Altnames: nikto-test.com
Ciphers: ECDHE-RSA-AES128-GCM-SHA256
Issuer: /C=US/O=Let's Encrypt/CN=Let's Encrypt Authority X3
+ Start Time: 2018-06-26 12:03:53 (GMT10)
---------------------------------------------------------------------------
+ Server: nginx/1.4.6 (Ubuntu)
+ Retrieved x-powered-by header: PHP/5.5.9-1ubuntu4.22
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'link' found, with multiple values: (
In the output we can see the items that were detected as interesting by Nikto. As well as the time taken for the scan and total number of items tested. If we review the web server logs we will be able to see the different items that were tested by the scanner.
Nikto and the Web Server
Lets review the web server logs. An important thing to understand when testing a site with Nikto is the amount of noise that this creates in the web server log files. Essentially Nikto is testing for the presence of thousands of possible web paths, and checking the response from the web server - which for most items will be a 404 not found.
Here is a sample from an Nginx web server being tested by Nikto.
203.xxx.xxx.xxx - - [25/Jun/2018:23:09:08 -0400] "GET /iissamples/sdk/asp/docs/Winmsdp.exe?Source=/IISSAMPLES/%c0%ae%c0%ae/default.asp HTTP/1.1" 404 16611 "-" "Mozilla/5.00 (Nikto/2.1.6) (Evasions:None) (Test:003021)" 203.xxx.xxx.xxx - - [25/Jun/2018:23:09:09 -0400] "GET /iissamples/exair/howitworks/Winmsdp.exe HTTP/1.1" 404 16611 "-" "Mozilla/5.00 (Nikto/2.1.6) (Evasions:None) (Test:003022)" 203.xxx.xxx.xxx - - [25/Jun/2018:23:09:10 -0400] "GET /%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5cwinnt%5cwin.ini HTTP/1.1" 404 16611 "-" "Mozilla/5.00 (Nikto/2.1.6) (Evasions:None) (Test:003023)" 203.xxx.xxx.xxx - - [25/Jun/2018:23:09:12 -0400] "GET /%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5cwinnt%5cwin.ini HTTP/1.1" 404 16611 "-" "Mozilla/5.00 (Nikto/2.1.6) (Evasions:None) (Test:003024)" 203.xxx.xxx.xxx - - [25/Jun/2018:23:09:13 -0400] "GET /conspass.chl+ HTTP/1.1" 404 16611 "-" "Mozilla/5.00 (Nikto/2.1.6) (Evasions:None) (Test:003025)" 203.xxx.xxx.xxx - - [25/Jun/2018:23:09:15 -0400] "GET /consport.chl+ HTTP/1.1" 404 16611 "-" "Mozilla/5.00 (Nikto/2.1.6) (Evasions:None) (Test:003026)" 203.xxx.xxx.xxx - - [25/Jun/2018:23:09:16 -0400] "GET /general.chl+ HTTP/1.1" 404 16611 "-" "Mozilla/5.00 (Nikto/2.1.6) (Evasions:None) (Test:003027)" 203.xxx.xxx.xxx - - [25/Jun/2018:23:09:18 -0400] "GET /srvstatus.chl+ HTTP/1.1" 404 16611 "-" "Mozilla/5.00 (Nikto/2.1.6) (Evasions:None) (Test:003028)"
Now unless your intrusion detection or server monitoring is broken, over 5000 of these sorts of hits in the web log will probably trigger a few alarms. Now it is very unlikely that these will cause an impact on the server, but it is certainly easy to spot. We can see the Nikto User Agent is in the log entry. Check the documentation to change the user agent.
Selecting the Target
Since the tool is checking for valid paths, it is important to remember that hitting a web server on different virtual host names, directly on the IP address and even on sub paths off the root of the site will give different results.
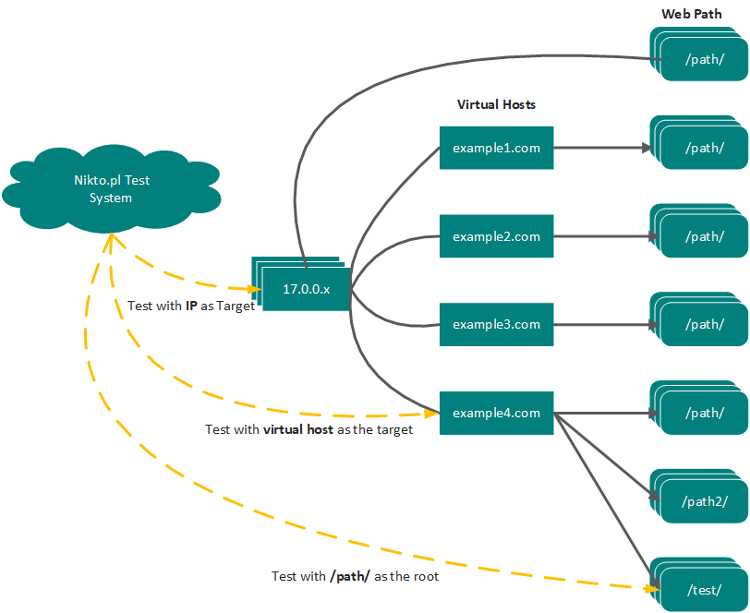
Lets take an example of PHPMyAdmin, this is a common tool for managing MySQL databases and can also be a good target for an attacker if it has not been patched or poorly managed. This application could be installed and available at https://2xx.xxx.xxx.xxx/phpmyadmin/ or https://mywebsite.com/phpmyadmin/ or http://mywebsite.com/admin/phpmyadmin/. So to find this application using Nikto we would have to target all three locations, and some servers might have hundreds of virtual hosts.
I am not suggesting running Nikto hundreds of times against every server, but consideration should be taken as to where to target the scan most effectively. Similar considerations come into play when performing simple file / directory brute forcing using Burp Suite or other web application testing tools.
Further information can be found in the documentation on the project page https://cirt.net/nikto2-docs/installation.html
Conclusion
Nikto continues to be an excellent web server testing tool, finding all sorts of obscure issues whether its directory indexing, admin panels or remote code execution in a rare web application. Take the time to run it and be surprised.
Next Level Your Technical Network Intelligence
Use Cases and More Info- 13 Vulnerability Scanners
- 17 Free DNS & Network Tools
- 4+ Billion Records of DNS / IP data
