DNS & IP Tools provide tactical intelligence to the Security Operation Center (SOC). Penetration Testers use the tools to map the attack surface of a target. Blue teams benefit from quickly identifying areas of security weakness and during incident response. Collect information about IP Addresses, Networks, Web Pages and DNS records.
The information gathering tools here are a quick reference point. Pivot from the information found with these tools to perform deeper enumeration using port scanners, web page analysis and other more aggressive tools.
In addition to the online access there is also the option to query the tools via an easy to use API, Maltego transforms and a Chrome extension.
Free IP and Network Tools
| Traceroute | Using mtr an advanced traceroute tool trace the path of an Internet connection. |
| Test Ping | A common tool for testing connectivity to a host, perform a ping from our server. |
| DNS Lookup | Find DNS records for a domain, results are determined using the dig DNS tool. |
| Find (A) Records | Find forward DNS (A) records for a domain. |
| Reverse DNS | Find Reverse DNS records for an IP address or a range of IP addresses. |
| Find Shared DNS Servers | Find hosts sharing DNS servers. |
| Zone Transfer | Online Test of a zone transfer that will attempt to get all DNS records for a target domain |
| Whois Lookup | Determine the registered owner of a domain or IP address block with the whois tool. |
| IP Geolocation Lookup | Find the geographic location of an IP address. |
| Reverse IP | Discover web hosts sharing an IP address with a reverse IP lookup. |
| TCP Port Scan | Determine the status of an Internet facing service or firewall |
| UDP Port Scan | Online UDP port scan available for common UDP services |
| Subnet Lookup Online | Determine the properties of a network subnet |
| HTTP Headers | View HTTP Headers of a web site. The HTTP Headers reveal system and web application details. |
| Page Links | Dump all the links from a web page. |
| AS Lookup | Get Autonomous System Number or ASN details from an AS or an IP address. |
| Banner Grabbing (Search) | Discover network services by querying the service port. |
| Chrome extension | Chrome Extension for Fast access to IP Tools. |
Many of these tools are passive in nature with no packets sent to target IP ranges. For tools that do generate a small number of packets against target networks there are benefits from not being sourced from your own IP range. Particular helpful in investigations or red team testing where you may benefit from not being directly attributable.
To balance the Free availability of these tools against the need to minimise abuse; a number of limits exist on the Free access to the IP Tools. Queries are are available through the web forms on each tool page. In addition access is also available using the simple API.
Remove Limits with a Full Membership
Reconnaissance and troubleshooting for technical operations.
- Unlimited Results (Free Queries are limited to 500 results)
- Generous Daily Quota (based on plan)
- Purchase additional Credits (Contact Sales for a Credit Boost!)
- Attack Surface Mapping with Domain Profiler
- Intelligence for Red Teams, Blue Teams and Network Operations
- Full Access to 28 Vulnerability Scanners & Tools

Using the IP Tools API
The aim of offering these tools via an API is to streamline access to vital information, simplifying the process of evaluating an organization's network security.
The output from the API is simple text or JSON for a number of endpoints. You can access the API using your client of choice such as curl, a web browser or a scripting language (php, python).
Using the API is straight forward, the target system IP address or hostname can be added to the query q= parameter. No key or sign-up is required for access to the Free API.
API Authentication for Members
As a member you get full access to the API endpoints. Find your API key in the user dashboard. Access with the API key must use HTTPS.
The API key can be used as a query parameter in the URL (&apikey=) or as a custom header in the HTTP request (X-API-Key).
Try for Free API access to the IP Tools using the endpoints listed below or Remove limits with a Full Membership.
Example requests with curl and a valid API Key:
curl "https://api.hackertarget.com/dnslookup/?q=hackertarget.com&apikey=plmoknijbuhvygvtrgedsfghhhhkjhkhfsk"curl -H "X-API-Key: zzzzzzaaaaaaaa" "https://api.hackertarget.com/whois/?q=hackertarget.com"Access to the MTR Traceroute API
https://api.hackertarget.com/mtr/?q=8.8.8.8&apikey=**APIKEYREQUIRED**
Access to the on-line Test Ping API
https://api.hackertarget.com/nping/?q=8.8.8.8&apikey=**APIKEYREQUIRED**
Access to the DNS Lookup API
https://api.hackertarget.com/dnslookup/?q=google.com
Access to Forward DNS (hostname) search API
The output is simply plain text and includes the IP address and the forward DNS host name. Data from the tool can be imported into a spreadsheet or other tool.
https://api.hackertarget.com/hostsearch/?q=example.comAccess to the Reverse DNS Lookup API
https://api.hackertarget.com/reversedns/?q=8.8.8.8
Access to the Whois Lookup API
https://api.hackertarget.com/whois/?q=8.8.8.8&apikey=**APIKEYREQUIRED**
Access to the IP Geolocation Lookup API
https://api.hackertarget.com/ipgeo/?q=8.8.8.8
Access to the Reverse IP Lookup API
https://api.hackertarget.com/reverseiplookup/?q=8.8.8.8
Access to the HTTP Headers API
https://api.hackertarget.com/httpheaders/?q=www.google.com
Access to the Page Links API
https://api.hackertarget.com/pagelinks/?q=www.google.com
Access to the AS Lookup API
https://api.hackertarget.com/aslookup/?q=1.1.1.1
Access to the Banner Search API
An easy to use simple API for quick access to our backend database. Use curl, python or even a browser against the API endpoint below to receive the results in json format.
https://api.hackertarget.com/bannerlookup/?q=2.2.2.2/24These tools have been made available for adhoc lookups to assist in the security assessment process. There is a limit of 50 API calls per day from a single IP address as a Free user. As some of the data from cached resources there is no guarantee made for accuracy or reliability of this service. See the HackerTarget.com terms of service for more information.
Rate Limiting of API Requests
To ensure service reliability we have a rate limit that amounts to a maximum of 2 requests per second from a single IP address. If you exceed the rate limit you will receive a HTTP 429 response code from the API server.API Usage and Quota Monitoring
The current users API quota and usage can both be monitored by examining the HTTP Headers of the response from the API endpoint. In the example below thecurl -i command is used, this will display the HTTP Headers as part of the output. The x-api-quota reports on the current users API quota and the x-api-count shows the current API usage count for the day.
test@thematrix:~$ curl -i https://api.hackertarget.com/geoip/?q=1.1.1.1 HTTP/2 200 server: nginx date: Wed, 27 Jan 2021 21:17:26 GMT content-type: text/plain; charset=utf-8 content-length: 91 x-api-quota: 51 x-api-count: 8 IP Address: 1.1.1.1 Country: Australia Latitude: -33.494 Longitude: 143.2104
Boost API Credits
Available now for all Members. The daily API quota is still used as your membership plan allows. If you are hitting your limit, we now offer an API Credit Boost for all membership levels. Pay a fixed price and receive a pool of credits to be used after your daily limit is reached. Contact sales for details and ordering.
Pssst!
Introductory pricing may increase.
$250 USD
100'000 API Credits
$1400 USD
1 Million API credits
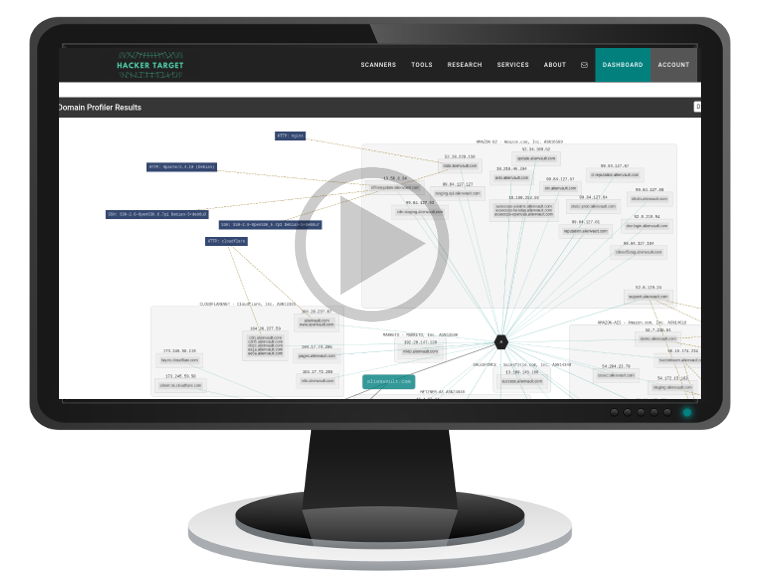
Domain Profiler for Attack Surface Discovery
Use the Domain Profiler tool to perform automated reconnaissance against a domain name. This provides a quick overview of an organisations Internet facing infrastructure within a few minutes.
Chrome Extension for Fast access to IP Tools
If you are a Chrome user you may find this extension helpful in your day to day work. Access all the IP Tools using a quick popup window that will be available after you install the extension.
If you are on a Windows box this is a great way to get easy access to helpful Linux command line tools (dig, whois, curl, wget).
Next Level Your Technical Network Intelligence
Get Access Now- 2.75 Billion Host A records
- 2.1 Billion Network Service Banners
- 2 Million Vulnerability Scans performed per year