What the Tool Does:
This basic guide shows you how to use the Banner Grabbing tool from HackerTarget to perform safe, passive reconnaissance.
The tool identifies services running on a target IP address by retrieving service banners: the text or metadata returned when an application responds to a connection. Results come from HackerTarget’s internet-wide scans, updated monthly (moving towards weekly), and are truncated for brevity. This makes it a quick and safe way to see what’s exposed without sending packets directly to the target.
For details on accuracy, data sources, and live confirmation options, see the Banner Grabbing Search page (About section)
What banners can reveal:
- Service type and version (e.g., OpenSSH 8.2, Apache/2.4.29)
- Web titles, TLS certificate details, and frameworks in use
Step 1: Prepare a target
Choose an IP address or CIDR range. If you only have a domain, resolve it first:
- Resolve domain ? IP with DNS Lookup
- Pick a single IP (e.g.,
140.82.121.4) or a range (e.g.,93.184.216.0/24).
Step 2 : Run the Banner Search
- Open hackertarget.com/banner-grabbing/
- Paste the IP or CIDR and click View Banners.
Example:
190.82.121.4 (An example IP)
Result:
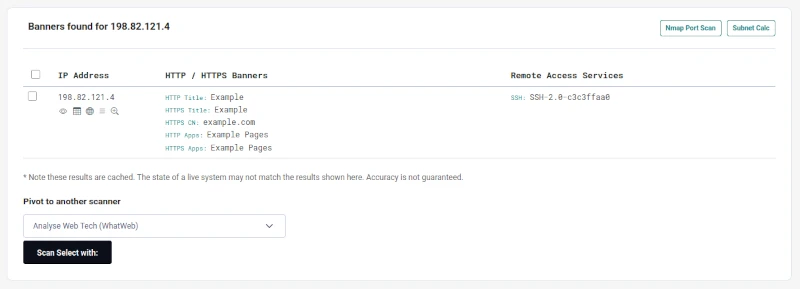
Step 3: Interpreting the results:
Typical output fields include:| Field | What it means | Why it matters | Example |
|---|---|---|---|
HTTP Title |
The title tag from the webpage | Quick check of what the site presents; can hint at default pages, frameworks, or brand names | example |
HTTPS CN Common Name |
Common name from the SSL/TLS certificate | Confirms the hostname the cert was issued for. Useful for spotting mismatches, expired, or fake certs. | example.com |
HTTPS O (Organisation) |
The “Organisation” field in the certificate. | Identifies the entity that owns the service. Good for attribution, OSINT and verifying legitimacy. | Example Foundation |
HTTP/HTTPS Apps |
Identified platform or framework | Reveals what frameworks are running e.g. GitHub Pages, WordPress, nginx. Can highlight exposure. | Example pages |
Remote Access Services |
Detected non-web services like SSH or FTP | Often expose banners with versions. Critical for defenders to audit and attackers to target. | SSH-2.0-OpenSSH_8.2p1 |
Banners |
The raw text string returned by a service. | May include software name, version, sometimes even hostnames or system info. | 220 smtp.example.com ESMTP Postfix |
Results are truncated at 50 characters, giving a quick overview of a network. Data is gathered from the HTML page at the server’s IP, not from virtual host applications.
Step 4: Quick actions to pivot on IP
Banner Grabbing gives you a first snapshot. Next is about chaining tools and confirming findings so you can build a complete picture of the target.
Under the IP you will see a row of icons. These are one-click pivots that run follow-up checks and show the results in a popup/side panel (except for Nmap). There’s also a copy button for fast sharing. These are active tools and send packets to live systems.
-
Nmap Port Scanner
Send the IP to the Nmap Port Scanner to actively check which ports and services are open in real time.
-
Reverse IP Lookup
Run a Reverse IP Lookup to discover all domains hosted on the same IP.
-
HTTP Headers
Headers can reveal server types, frameworks (
X-Powered-By: PHP/7.4), and security controls (Strict-Transport-Security,X-Frame-Options). -
Page Links Extractor
If a web service is found, use the Page Links Extractor to crawl visible links and explore the site’s structure.
-
Analyze Web Tech
If banners show HTTP/HTTPS services, pivot into the Analyse Web Tech (WhatWeb) tool to fingerprint frameworks, CMS, and libraries.
How to use the API to access the Banner Search
A simple API for quick access to our backend database. Use curl, python or even a browser against the API endpoint below to receive the results in json format.
API Example using curl:
$ curl https://api.hackertarget.com/bannerlookup/?q=8.8.8.8
Result:
{
"ip": "8.8.8.8",
"https": {
"title": "302 Moved",
"server":
"HTTP server (unknown)",
"cn": "dns.google",
"alt_n": [
"dns.google",
"dns.google.com",
"*.dns.google.com",
"8888.google",
"dns64.dns.google"
],
"redirect_location": "https://dns.google/"
}
}
