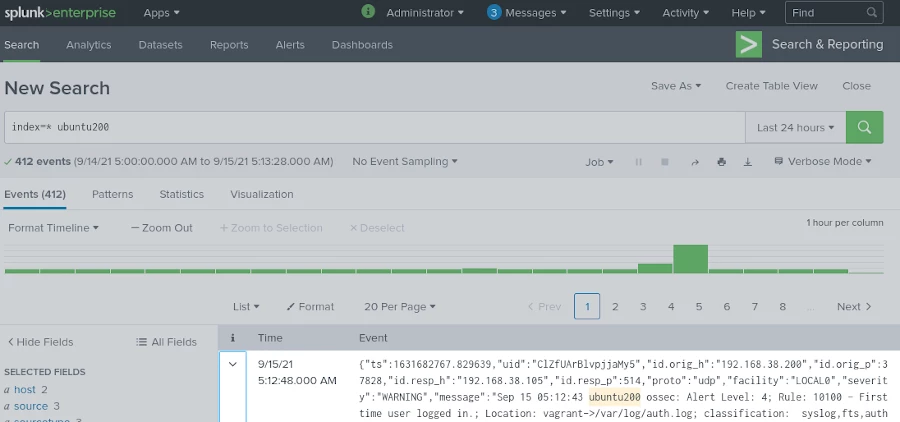
DetectionLab is a fantastic project by Chris Long for quickly deploying a Windows Domain-based test environment with Linux-based Security Information Event Management (SIEM). See our DetectionLab Tutorial or check out the project page for more information.
The idea is to be able to quickly deploy a Linux server that has agents (ossec / osquery) pre-installed for security monitoring, with the agents sending data back to the DetectionLab logger host.
Vagrant Configuration File
The basis for adding additional hosts to the DetectionLab network is the Vagrant configuration file. If you have not used Vagrant, then getting things working in a test environment is not difficult. A little bit of knowledge will go a long way, and you will find yourself using Vagrant for other tasks as it simply saves you time.
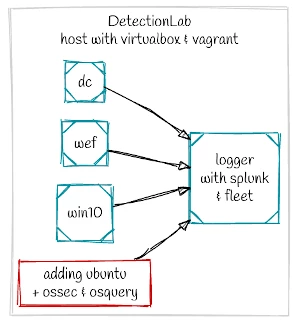
Digging into the Vagrant configuration and deployment, we find that the configuration file is configured to:
- Deploy an Ubuntu server that connects to the DetectionLab Network (192.168.38.0/24)
- Installs osquery agent and connects to the Fleet Manager
- Install ossec agent, configured to send logs to UDP 514 Syslog on Splunk
- Updates Splunk to enable the UDP Syslog Input
- Splunk is now collecting security events from the Ubuntu Server (indexing both osquery and ossec events)
Hopefully, this sample configuration highlights the time saving benefits of using Vagrant within your lab environment. All these tasks are performed automatically and after the operating system is deployed, with only a few configuration files.
Using this configuration it will be straightforward to modify the parameters and shell commands to generate custom systems that suit your own environment.
Reading through the configuration file there is nothing overly complex. One point to highlight is the curl commands that retrieve a JWT token from the fleetdm server (using default credentials). Using these credentials the second curl command downloads the client certificate so that osquery can connect to Fleet.
Deploying the Ubuntu Host
To get started grab the Vagrantfile, secret.txt, ossec.conf and flagfile.txt from Github. Modify the host name and IP address as required if you are deploying multiple systems.
Hostname: ubuntu200
IP Address: 192.168.38.200
test@vbox:~/$ git clone https://github.com/hackertarget/DetectionLabUbuntuAddon/ test@vbox:~/$ cd DetectionLabUbuntuAddon test@vbox:~/DetectionLabUbuntuAddon$ vagrant up
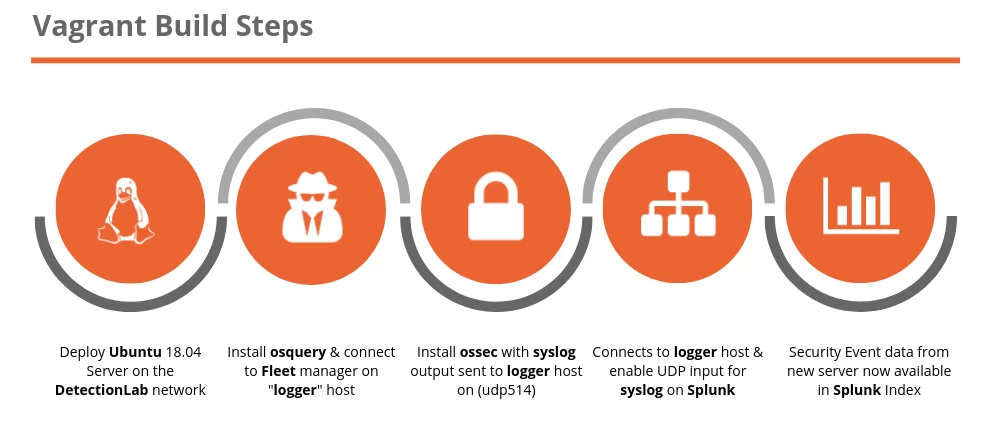
This will start up the host, add it to the network and install ossec and osquery. Log into the fleetdm console to see if the host (ubuntu200) has connected successfully.
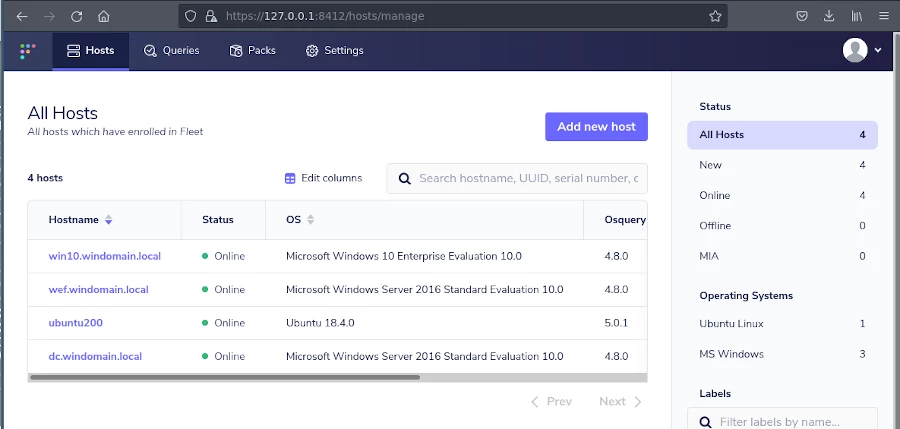
And in this screenshot we can see ossec alerts being indexed in Splunk from the ubuntu200 host.