There are ways to detect and defend. Here we have provided 3 examples of free and open source ways to detect these threats on Linux based systems: RKHunter, Chkrootkit and OSSEC Rootcheck.
rkhunter
rkhunter or Rootkit Hunter is opensource software which scans for rootkits, backdoors, sniffers and exploits.
Install rkhunter
Installing it on a clean Ubuntu 20.04 LTS
$ sudo apt install rkhunter
Options
Available options can be seen with -h or --help. Below are the first few options, there are many others to check out.
$ sudo rkhunter -h
Usage: rkhunter {--check | --unlock | update | --versioncheck |
--propupd [{filename | directory | package name},...] |
--list [{tests | {lang | languages} | rootkits | perl | propfiles}] |
--config-check | --version | --help} [options]
Current Options are:
--append-log Append to the logfile, do not overwrite
--bindir directory>... Use the specified command directories
-c, --check Check the local system
-C, --config-check Check the configuration file(s), then exit
--cs2, --color-set2 Use the second color set for output
---More Options---
Check the version with the -V
$ sudo rkhunter -V Rootkit Hunter 1.4.6 This software was developed by the Rootkit Hunter Project team. Please review your rkhunter configuration files before using. Please review the documentation before posting bug reports or questions ...
--list List the available test names, languages, rootkit names, per module status of file properties databases
$ sudo rkhunter --list
How to use Rkhunter
Use -c or --check to run a check on the local system.
$ sudo rkhunter -c
In this instance, the result was an error. Instead of getting a report on the rootkit system check, the following was returned;
Invalid SCRIPTWHITELIST configuration option: Non-existent pathname: /usr/bin/egrep Invalid SCRIPTWHITELIST configuration option: Non-existent pathname: /usr/bin/fegrep
Simple to resolve. The grep binaries are not at that path - so they cannot be whitelisted. Change to a comment in rkhunter.conf file as suggested here (helpful forum ).
#Invalid SCRIPTWHITELIST configuration option: Non-existent pathname: /usr/bin/egrep #Invalid SCRIPTWHITELIST configuration option: Non-existent pathname: /usr/bin/fegrep
Note from the developers in the .conf -- "recommended that the command rkhunter -C is run after any changes have been made"
$ sudo rkhunter -C
Start system check again
$ sudo rkhunter -c
Rewarded with a satisfyingly flow of data. The below screenshot shows a snapshot of the results.
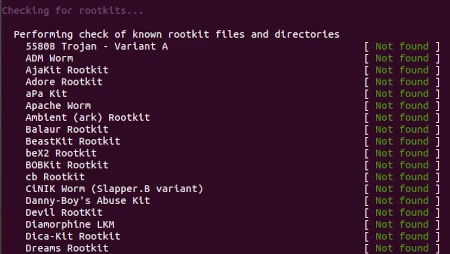
Below shows the final summary.
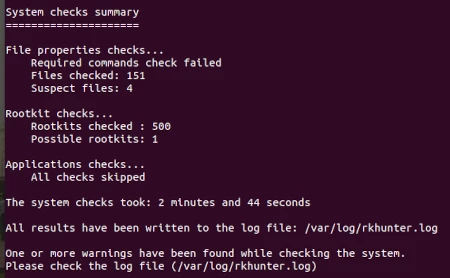
As noted above - 1 or more warnings have been found while checking the system. Check the log file /var/log/rkhunter.log for more info.
chkrootkit
chkrootkit (Check Rootkit) is free and open source. At the time of writing, chkrootkit version 0.55 released Jun 2021.
Install chkrootkit
It can be easily installed with sudo apt install chkrootkit
$ sudo apt install chkrootkit
Options
Options can be shown with -h
$ sudo chkrootkit -h
Usage: /usr/sbin/chkrootkit [options] [test ...]
Options:
-h show this help and exit
-V show version information and exit
-l show available tests and exit
-d debug
-q quiet mode
-x expert mode
-e exclude known false positive files/dirs, quoted,
space separated, READ WARNING IN README
-r dir use dir as the root directory
-p dir1:dir2:dirN path for external commands used by chkrootkit
-n skip NFS mounted dirs
How to use chkrootkit
It needs root privileges to run and is as simple as;
$ sudo chkrootkit
The scanning is very quick. Below is a snippet of the results.
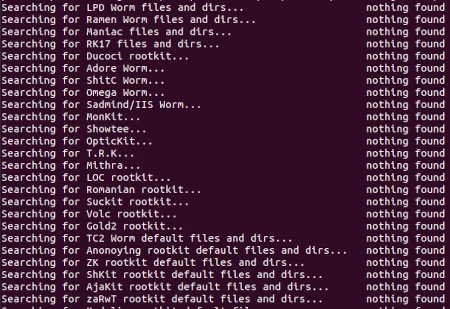
To be more targeted in the search, have a look at the options in the -h help menu
-q quiet mode -- in which only output messages with 'infected' status show.
$ sudo chkrootkit -q
Without quiet mode -q enabled, a selection of the following messages are printed to the screen as part of the results.
Not infected: no known rootkit signature located.
Infected: the scan identified a command probably modified by a known rootkit.
Not found: command to be tested in not available.
Not tested: test not performed.
Vulnerable but disabled: command infected by not in use.
chkrootkit does not export the results to a log file by default as rkhunter does, however, it is a simple matter of using the following command to create a file of results. The file name can be whatever suits the user.
$ sudo chkrootkit > chkrootkit-results
The two tools discussed above, rkhunter and chkrootkit, scan files for rootkits and provide information on what is infected. These are detection tools - they do not remove them. It is also worth highlighting the likelihood of false positives. It is necessary to run additional checks, investigate the results, and follow up with an alternative scan before taking any drastic remediation.
OSSEC RootCheck
OSSEC is an open source Host-based Intrusion Detection System (HIDS) and comes with a rootkit detection module. According to OSSEC's documention: "...OSSEC HIDS will perform rootkit detection on every system where the agent is installed"
OSSEC provides several functions
- Real time log monitoring.
- File integrity checking - detects changes to files and system paths.
- Rootkit detection.
- Changes to the system / running services (netstat) / disk space / password file changes.
- Real time blocking of detected attacks through firewall rule modification.
- Execute arbitrary commands based on specific events.
OSSEC uses a variety of methods to detect rootkits. It is a more indepth tool. Check out our Introduction and install guide to OSSEC to get started.
