Use Nmap to find open ports on Internet facing systems with this online port scanner.
Test servers, firewalls and network perimeters with Nmap Online providing the most accurate port status of a systems Internet footprint. It is simply the easiest way to perform an external port scan.
Free Port Scan to check any IP address and test 10 common TCP ports with Nmap version detection (-sV) enabled. Once you see how easy it is grab a membership and get immediate full access.
21 File Transfer (FTP) 22 Secure Shell (SSH) 23 Telnet 25 Mail (SMTP) 80 Web (HTTP) 110 Mail (POP3) 143 Mail (IMAP) 443 SSL/TLS (HTTPS) 445 Microsoft (SMB) 3389 Remote (RDP)
Membership Benefits
Access advanced network mapping and regular scan schedules.
Advanced Nmap
Scan all ports and subnets.
Schedule daily scans
Be alerted on changes.
Access Granted
To 27 Vulnerability Scanners & IP Tools.
Target Lists
Submit a list of targets for port scanning.
Simplified Reporting
Export to XLSX.
IPV6
Test IPv6 connected systems.
Here are 6 use cases for Nmap & our Online Port Scanner
- Determine status of host and network based firewalls
- Understanding the results from the online Nmap scan will reveal whether a firewall is present. The
shodan.iosearch engine finds millions of poorly configured firewalls on a daily basis. - Test Firewall Logging and IDS
- Launch remote scans against your infrastructure to test that your security monitoring is working as expected. Review firewall logging and Intrusion Detection System alerts.
- Find Open Ports on Cloud based Virtual Servers
- In 2016 thousands of MongoDB databases were compromised and data leaked due to the server being configured to listen on the Internet facing Interface. Using an online port scanner it is possible to quickly identify a host firewall with holes or services poorly configured.
- Detect Unauthorized Firewall Changes
- When your firewall rule base changes require change board approval. A scheduled Nmap Port Scan can quickly determine firewall changes that have not been through the change approval process.
- Not all Firewalls work well with IPv6
- As IPv6 gets deployed it is important to understand whether the IPv6 interface has the same level of protection as the existing IPv4 addresses. Many virtual servers (VPS) are deployed with IPv6 enabled by default. Have you checked yours?
- Troubleshoot Network Services
- Your getting pushed to roll out the new service. The network guys are saying its not their problem, and the firewall administrator is pointing the finger at the developers. Sometimes you just need to know if the port is open and listening.
Know when your attack surface changes
Schedule Nmap to monitor all your network assets
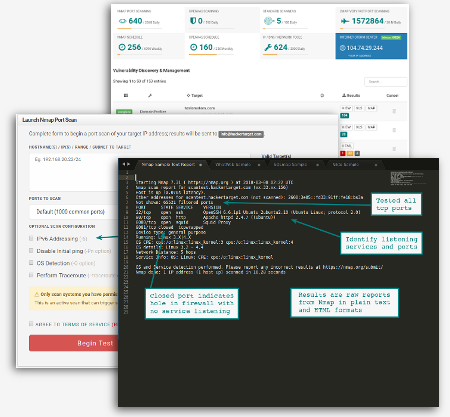
Launch an Online Nmap Port Scan in 3 Simple Steps
Fill out the form; entering the address or hostname of the target(s)
Enter a public IP address or hostname that is accessible from an external Internet facing perspective. You must have permission to scan the target. Online Nmap port scans can also be performed against a list of valid target addresses; simply include the targets comma separated or as a list with line breaks.
Scan a single IP address or Hostname
Example:
192.168.1.1
example.com
Scan a range of IP addresses
Example:
192.168.1.0/24
192.168.1.1-50
Members can select the Combine Report option to receive a single report which includes a summary table of the multiple NMAP targets requested, and the full results all presented in a single file.
Decide on which Ports you wish to Scan
Select the port option based on standard Nmap options; Default, Fast scan (-F) or Scan All 65535 ports on an IP Address. Scanning all ports is the most accurate way to discover every listening service. A full scan with all ports is required for a comprehensive test of a firewall configuration. Note that a full scan can take from 20 minutes to a couple of hours depending on the network.
Also available is scanning of common UDP ports, as well a custom port configuration option where you may select a subset of specific ports (udp or tcp).
Optional Configuration
- Default protocol is IPv4, select the Protocol option to enable IPv6 (nmap option -6)
- Ping is performed by default to ensure system is responding, select option to disable the ping (nmap option -Pn)
- Enable OS Detection to probe the Operating System version (nmap option -O)
- Perform an optional Traceroute uses results from the port scan to find the most accurate method (nmap option --traceroute)
The Final Step is to Launch and await the results of the Port Scan
Actual scan times will vary greatly depending on the target network and number of ports being scanned.
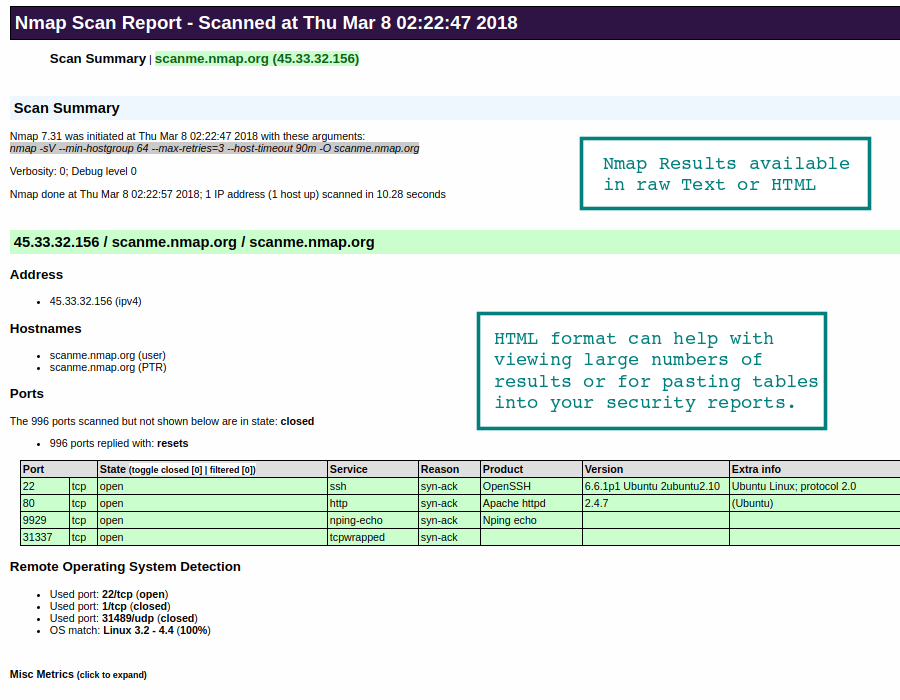
Nmap results are delivered to your registered email address once the port scan is completed. Results are also available in the Members Dashboard for download. Improve your security reporting workflow with an easy to use export to XLSX option for all open ports. Generate summary reports across multiple scan profiles and/or networks.
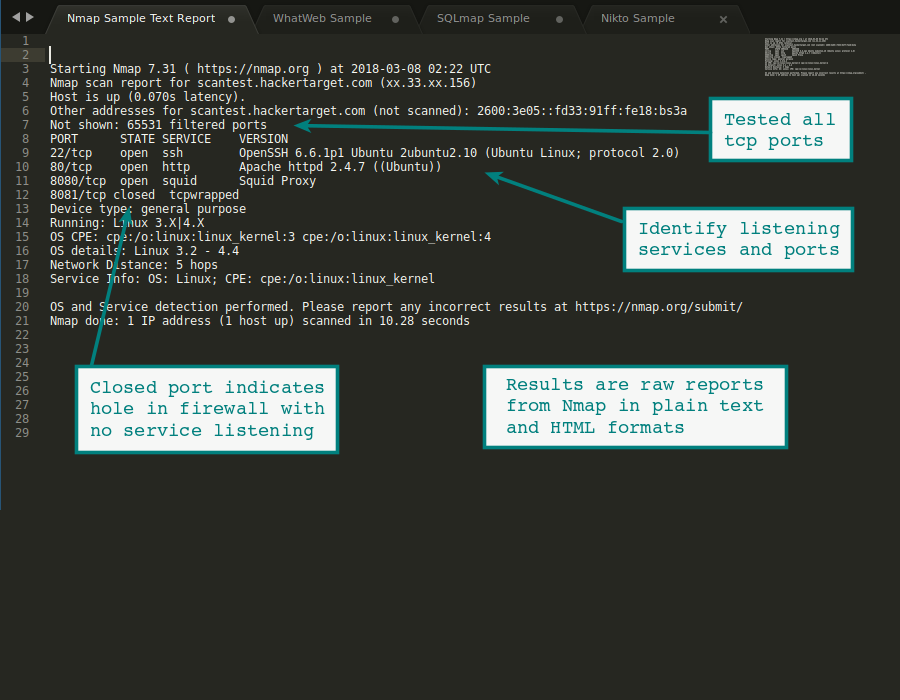
Sample Results from Nmap Online
The default settings will perform the port scan using a TCP SYN based test. This is a standard Nmap port scan (-sS) with version detection enabled (nmap -sV). Any other selected optional parameters will be included.
The results are emailed to the users registered email address. Scan results are available as plain text and HTML formats.
About the Nmap Port Scanner Software
Nmap is a network port scanner that tests network connectivity between different hosts and services. Firewalls, Router ACL’s and other factors can impact a network based connection.
Initially Nmap was a simple but powerful tool that enabled the scanning of networks or individual hosts to determine if there were services running and if a firewall was present. Modern versions of Nmap have extended capabilities including a built in scripting language (NSE) that can perform a multitude of additional checks against any services found to be open. The ever growing list of NSE scripts has pushed Nmap into the realm of a fast light weight vulnerability scanner.
Download Nmap today from insecure.org, it is available in versions for Windows (XP, 2003, 2008, 2012) and Linux / FreeBSD. Zenmap is a graphical front end for those not comfortable on the command line. When installing Nmap I encourage you to download from the source as it is constantly being improved and built upon. Linux distributions will not always have the latest version in the package repository.