Understand the Port Scanning Process with this Nmap Tutorial
With a basic understanding of networking (IP addresses and Service Ports), learn to run a port scanner, and understand what is happening under the hood.
Nmap is the world's leading port scanner, and a popular part of our hosted security tools. Nmap, as an online port scanner, can scan your perimeter network devices and servers from an external perspective ie outside your firewall.
Getting started with Nmap
Windows or Linux?
Use the operating system that works for you. Nmap will run on a Windows system, however, it generally works better and is faster under Linux, so that would be my recommended platform. Plus, having experience with Linux based systems is a great way to get access to a wide selection of security tools.
The installation steps in this guide are for an Ubuntu Linux based system but could be applied, with minor changes, to other Linux flavors such as Fedora / Centos, or BSD based system.
If you are not using a Linux based system as your main operating system, you will find it convenient and simple to fire up an installation of Ubuntu Linux in a virtual machine. You will then be able to the installation, play with Linux, and break things without affecting your base system. If you are interested in doing remote scanning such as that provided by hackertarget.com, you could get a cheap Ubuntu based VPS from one of the hundreds of providers, paying anything from $10 per month to $100 or so. Linode is great for this, providing high quality and good specifications for the price.
Step 1: Operating System Installation
If you need to get a Linux system up and running, a Free virtual machine is Virtualbox. This is an easy to use virtual machine system, you could of course alternatively use VMware or Parallels.
I suggest selecting bridged network for your adapter - this will give your virtual machine an IP address on your local network. Then when you are playing with Nmap you can scan your local virtual machine on one IP, your base operating system on another IP, and other devices on your local network. Scanning is fun, just keep in mind it is intrusive. Only scan systems you own/operate or have permission to scan.
Step 2: Ubuntu Installation
Download the latest Ubuntu iso from www.ubuntu.com, select the ISO as the boot media for your guest and start the virtual machine. Select the install option and Ubuntu will be installed onto the virtual hard disk on the machine.
Step 3: Nmap Installation from source
Ubuntu comes with Nmap in the repositories or software library, however this is not the one we want. In most cases, I suggest sticking with the software from the Software Center, but in this case, there are many benefits from running the latest version of Nmap.
On the download page https://nmap.org/download.html you will see the bzip2 version (you can get the stable or development).
To get the latest feature packed development version, start a terminal (type terminal in the menu of Ubuntu and it will show as an option):
wget http://nmap.org/dist/nmap-5.61TEST5.tar.bz2
Hopefully Internet access from your virtual machine is working, if it is you will soon have the latest in your home directory.
You may need to install g++ in order to compile. You should also install the libssl-dev package as this will enable the SSL testing NSE scripts to work.
sudo apt-get install g++
Now unpack, compile and install. Use the standard configure and make commands when building software from source.
tar jxvf nmap-5.61TEST5.tar.bz2 cd nmap-5.61TEST5/ ./configure make make install
Run the nmap commmand to show available command line options if the installation has been successful.
testuser@ubuntu8:/~$nmap
Nmap 5.61TEST5 ( https://nmap.org )
Usage: nmap [Scan Type(s)] [Options] {target specification}
TARGET SPECIFICATION:
Can pass hostnames, IP addresses, networks, etc.
Ex: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254
-iL : Input from list of hosts/networks
-iR : Choose random targets
--exclude : Exclude hosts/networks
--excludefile : Exclude list from file
HOST DISCOVERY:
-sL: List Scan - simply list targets to scan
-sn: Ping Scan - disable port scan
-Pn: Treat all hosts as online -- skip host discovery
-PS/PA/PU/PY[portlist]: TCP SYN/ACK, UDP or SCTP discovery to given ports
-PE/PP/PM: ICMP echo, timestamp, and netmask request discovery probes
-PO[protocol list]: IP Protocol Ping
-n/-R: Never do DNS resolution/Always resolve [default: sometimes]
--dns-servers : Specify custom DNS servers
--system-dns: Use OS's DNS resolver
--traceroute: Trace hop path to each host
SCAN TECHNIQUES:
-sS/sT/sA/sW/sM: TCP SYN/Connect()/ACK/Window/Maimon scans
-sU: UDP Scan
-sN/sF/sX: TCP Null, FIN, and Xmas scans
--scanflags : Customize TCP scan flags
-sI : Idle scan
-sY/sZ: SCTP INIT/COOKIE-ECHO scans
-sO: IP protocol scan
-b : FTP bounce scan
PORT SPECIFICATION AND SCAN ORDER:
-p : Only scan specified ports
Ex: -p22; -p1-65535; -p U:53,111,137,T:21-25,80,139,8080,S:9
-F: Fast mode - Scan fewer ports than the default scan
-r: Scan ports consecutively - don't randomize
--top-ports : Scan most common ports
--port-ratio : Scan ports more common than
SERVICE/VERSION DETECTION:
-sV: Probe open ports to determine service/version info
--version-intensity : Set from 0 (light) to 9 (try all probes)
--version-light: Limit to most likely probes (intensity 2)
--version-all: Try every single probe (intensity 9)
--version-trace: Show detailed version scan activity (for debugging)
SCRIPT SCAN:
-sC: equivalent to --script=default
--script=: is a comma separated list of
directories, script-files or script-categories
--script-args=: provide arguments to scripts
--script-args-file=filename: provide NSE script args in a file
--script-trace: Show all data sent and received
--script-updatedb: Update the script database.
--script-help=: Show help about scripts.
is a comma separted list of script-files or
script-categories.
OS DETECTION:
-O: Enable OS detection
--osscan-limit: Limit OS detection to promising targets
--osscan-guess: Guess OS more aggressively
TIMING AND PERFORMANCE:
Options which take
You now have a list of the various options available. Start with the basics then move onto testing different scan options and NSE scripts. You have found the white rabbit, are you going to follow?
As you can see, there are a great many variations on port scanning that can be done with Nmap. Hit the book in the column to the right for an in-depth guide.
Nmap command example
This is a simple command for scanning your local network (class C or /24):
nmap -sV -p 1-65535 192.168.1.1/24
This command will scan all of your local IP range (assuming your in the 192.168.1.0-254 range), and will perform service identification -sV and will scan all ports -p 1-65535. Running this as a normal user, and not root, it will be TCP Connect based scan. If the command is run with sudo at the front, it will run as a TCP SYN scan.
Zenmap for those who like to click
Start zenmap either from the command line or through the menu. This is the GUI interface to the Nmap scanner. It is solid and works, I prefer the command line as it allows you to script things, collect the output and have more understanding of what's going on. One nice feature of the Zenmap scanner is the graphical map of the scanned networks, a bit of eye candy if nothing else.
Understanding Open, Closed and Filtered
Nmap has a variety of scan types. Understanding how the default and most common SYN scan works is a good place to start to examine how the scan works and interpreting the results.
The 3 way TCP handshake
First, a bit of background, during communication with a TCP service, a single connection is established with the TCP 3 way handshake. This involves a SYN sent to an TCP open port that has a service bound to it, typical examples are HTTP (port 80), SMTP (port 25), POP3 (port 110) or SSH (port 22).
The server side will see the SYN and respond with SYN ACK, with the client answering the SYN ACK with an ACK. This completes the set up and the data of the service protocol can now be communicated.
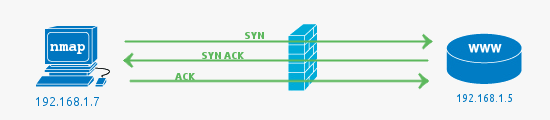
In this example, the firewall passes the traffic to the web server (HTTP -> 80) and the web server responds with the acknowledgement.
In all these examples a firewall could be a separate hardware device, or it could be a local software firewall on the host computer.
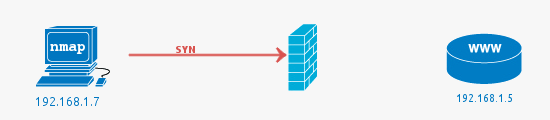
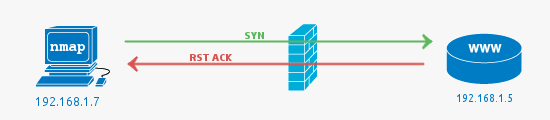
Filtered ports or when the Firewall drops a packet
The job of a firewall is to protect a system from unwanted packets that could harm the system. In this simple example, the port scan is conducted against port 81, as there is no service running on this port, using a firewall to block access to it is best practice.
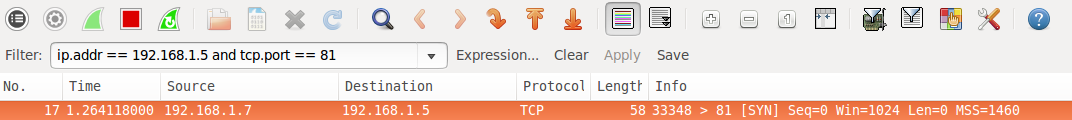
A filtered port result from Nmap indicates that the port has not responded at all. The SYN packet has simply been dropped by the firewall. See the following Wireshark packet capture that shows the initial packet with no response.
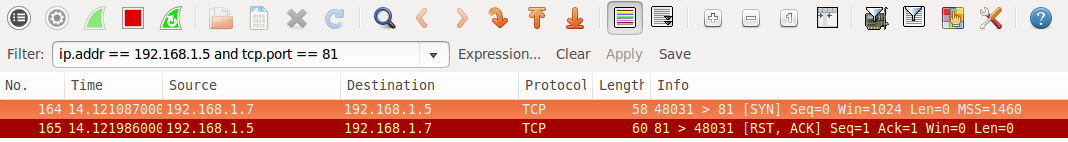
Closed ports or when the Firewall fails
In this case, closed ports most commonly indicate there is no service running on the port, but the firewall has allowed the connection to go through to the server. It can also mean no firewall is present at all.
Note that while we are discussing the most common scenarios, it is possible to configure a firewall to reject packets rather than drop. This would mean packets hitting the firewall would be seen as closed (the firewall is responding with RST ACK).
Pictured below is a case where a firewall rule allows the packet on port 81 through even though there is no service listening on the port. This is most likely because the firewall is poorly configured.
An Open Port (service) is found
Open Ports are usually what you are looking for when kicking off Nmap scans. The open service could be a publicly accessible service that is, by its nature, supposed to be accessible. It may be a back-end service that does not need to be publicly accessible, and therefore should be blocked by a firewall.
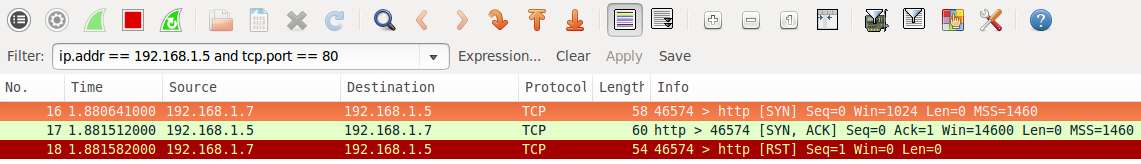
An interesting thing to notice in the wireshark capture is the RST packet sent after accepting the SYN ACK from the web server. The RST is sent by Nmap as the state of the port (open) has been determined by the SYN ACK if we were looking for further information such as the HTTP service version or to get the page, the RST would not be sent. A full connection would be established.
Hacking Nmap Video from Defcon 13
This video contains some interesting Nmap features, the presenter is Fyodor the creator of the Nmap port scanner.
Vulnerability Scans and Network Intelligence
Use CasesEnumerate and Discover
Know the Network
28 vulnerability scanners and network tools
Membership
