When assessing the network security of an organization it is important to understand the breadth of the attack surface. A single forgotten host or web application in the network will often become the initial foothold for an attacker.
Passively Mapping the Network Attack Surface
Using open source intelligence (OSINT) techniques and tools it is possible to map an organizations Internet facing networks and services without actually sending any packets (or just a few standard requests) to the target network.
Open source intelligence (OSINT) is defined as deriving intelligence from publicly available resources.
Consider the following graphic; you will notice that as the analysis is progressed, newly discovered items (IP address / host names / net blocks) can open up new areas to explore (and attack).
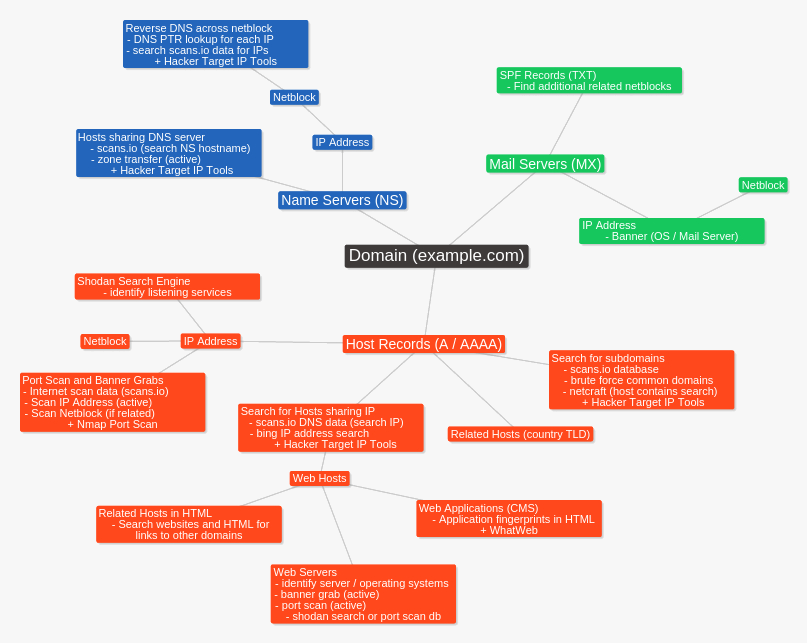
Identifying all known hosts for an organization allows us to continue to dig deeper for more systems and hosts to target. By examining all discovered IP address blocks (ASN) we can find other hosts within the net block of interest. Identifying related domains will lead to the discovery of more hosts.
Think of a single web server; the actual open services (ssh, http, rdp) are all points of attack; discovering all the virtual hosts running on the server is also important as web applications running on any of the virtual hosts are also an attack vector.
Basic DNS queries
Most domains will have a web site, mail server and dns servers associated with it. These will be our initial point of reference when discovering the attack surface. We can use DNS lookup tools and whois to find where the web (A records), mail (MX records) and DNS (NS records) services are being hosted.
hackertarget.com. 3600 IN A 178.79.163.23 hackertarget.com. 3600 IN AAAA 2a01:7e00::f03c:91ff:fe70:d437 hackertarget.com. 3600 IN MX 10 aspmx.l.google.com. hackertarget.com. 3600 IN MX 20 alt1.aspmx.l.google.com. hackertarget.com. 3600 IN MX 20 alt2.aspmx.l.google.com. hackertarget.com. 3600 IN MX 30 aspmx2.googlemail.com. hackertarget.com. 3600 IN NS ns51.domaincontrol.com. hackertarget.com. 3600 IN NS ns52.domaincontrol.com.
Initial Host discovery (Google, Bing and Netcraft)
A simple search for all host names related to the target domain is also a good starting point. Using search engines such as Google (site:example.com) and Bing (site:example.com) can reveal sub-domains and web hosts that may be of interest.
When searching with Google if there are a large number of results you can remove the known domains with the following query.
site:example.com -site:www.example.com
Google Hacking is a well documented technique that involves getting Google to reveal technical information that is of interest to an attacker. The Google hacking database is the best place to get started if you are not familiar with this technique.
Another handy tool is the netcraft host search. Enter the domain as your search term (be sure to include the . before your domain name to only get sub-domains of your target domain. You can see the Netcraft search provides a quick overview of known web hosts for the domain and the net blocks that they are hosted in. Another interesting piece of information is the historical data, Netcraft have been collecting this data for a long time.
Finding more hosts through data mining DNS records
Passive DNS reconnaissance allows discovery of DNS host records without actively querying the target DNS servers. If DNS monitoring is in place active dns recon could be detected by the target. Techniques that can be classed as active DNS recon include brute forcing common sub-domains of the target or attempting DNS zone transfers (query type=AXFR).
There are many on line resources for passive DNS analysis and searching, rather than sticking to regular DNS lookups we can perform large scale searches using DNS data sets. One such resource is that provided by scans.io.
the scans.io data
Scans.io and Project Sonar gather Internet wide scan data and make it available to researchers and the security community. This data includes port scans and a dump of all the DNS records that they can find.
Using the DNS records dump you can search through over 80GB of DNS data for all entries that match your target domain. If you do not wish to go through the trouble of downloading and extracting such a large chunk of data you can use our free tools to get started with your network reconnaissance.
Name Servers (type=NS)
The location of the DNS servers may be internal to the organization network or as is often the case they be a hosted service. This can be often be determined by simply looking up the net block owner (ASN) of the IP address of the DNS server.
When looking at DNS servers we can not only review the Host (A) records that point to the IP address of the DNS server but also do a reverse search across DNS data for all hosts that use the same DNS server. In a hosted situation this may not be as valuable but if its an internal company DNS server we will quickly identify all related domains for the organization (that are at least using this DNS infrastructure).
targetdomain.com
targetdomain.co.uk
targetdomain.net
forgotten-footy-tipping-site-with-no-security-controls.com
vpn.targetdomain.com
webmail.targetdomain.com
SPF Records (type=TXT)
Sender Policy Framework is configured through the TXT DNS record. If configured this will contain all servers (or networks) that are allowed to send email from the domain. This can often reveal IP addresses (and net blocks) of the organization that you may not have been aware of.
hackertarget.com. 3600 IN TXT "v=spf1 include:_spf.google.com ip4:178.79.163.23 ip4:66.228.44.129 ip4:173.255.225.101 ip4:66.175.214.247 ip6:2a01:7e00::f03c:91ff:fe70:d437 ip6:2600:3c03::f03c:91ff:fe6e:d558 include:_spf.google.com ~all"
Reverse DNS across IP blocks of Interest
Once you have a list of all IP addresses and ASN's of interest you can attempt to find more active hosts within those net blocks that the organizations owns or has assets within. A good way of finding more hosts is to perform a reverse DNS search across the full net blocks of interest.
178.79.x.22 host4.example.com
178.79.x.23 targetdomain.com
178.79.x.24 forgotten-unpatched-dev-host.targetdomain.com
178.79.x.25 host6.example.com
Finding Web Servers
When it comes to mapping a network the web servers of an organization open up a wide attack surface. They also contain a wealth of information, not just published but insights into the technologies in use, operating systems and even how well managed the information technology resources of the organization are.
To map the attack surface of a web server it is important to consider the available network services, the virtual hosts (websites) and the web applications in use.
Identifying all virtual web hosts on the web server is an important part of the information gathering process. Different web sites on the same web server will often be managed using different content management systems and web applications. A vulnerability in any of these web applications could allow code execution on the web server.
To identify the virtual web hosts on a particular IP Address there are a number of well known web based tools such as Bing and Robtex. An IP address search using the ip:1.1.1.1 search term on the Bing search engine will reveal all web sites that Bing has in its index that point to that same IP address. Experience shows this is a good starting place but like the Bing search engine in general, can contain stale entries and limited results.
As previously mentioned scans.io regularly compiles all the DNS data it can publicly find, we can use this data to identify the web server hosts (A records). By searching for an IP address in all the known DNS records, we can find all the hosts that resolve to that IP. This is the method we use for the Reverse IP Address Search tool we created and also parts of the dnsdumpster.com project.
Other Network Services
In any vulnerability assessment, it is essential to identify all listening services. A web server will of course usually have a web server (port 80), an ftp server will have an FTP service (port 21) and a mail server will be listening for mail (smtp on 25, pop3 on 110, imap on 143 and more).
It is important to discover all the listening services to determine if they are vulnerable to exploitation or authentication attacks.
Traditionally these services would be identified using Port Scans with tools such as the Nmap Port Scanner. Of course, using a port scanner is no longer a passive undertaking, as using a tool such as Nmap involves sending packets to the target systems.
shodan.io search engine
To passively find open services and the banners for the open services we can use the shodan.io search engine. From the banners of services such as web servers, mail and ftp we are able to identify the version of the server software running the service and often the operating system of the server. All without sending any packets to the target organization.

Becoming the attacker and the Next Steps
Putting yourself in the shoes of an attacker and attempting to map out an organization's Internet-facing systems is a great way to develop an understanding of the attack surface of a network. To start, find all the public IP addresses of known hosts for a domain and expand this to include net blocks of interest that are hosting these services. Now, try to find all virtual host-names hosted on the IP addresses. From this, you can map out the web applications in use.
From this initial passive analysis, it may be possible to identify vulnerable or possibly vulnerable points in the network. This can inform your next steps on where to focus your attack or vulnerability assessment.
The Next Steps
Moving on from passive analysis, the next steps to consider are active information gathering such as DNS zone transfers or sub-domain brute forcing. Followed by active network scanning such as Nmap Port Scans and vulnerability scanning.
Ultimately the next steps will be determined by your scope and purpose for the performing the analysis.
See a complete list of our Free IP and Network Testing tools.
Discover - Explore - Learn.
Professional Attack Surface Assessment
Zero Impact. Know Your Internet Footprint.
