The Vulnerability Scanner
The primary use for a vulnerability scanner is to perform a sanity check against the Attack Surface. The goal is to determine if there were any security issues missed during deployment or ongoing operations.
What is a Vulnerability Scanner?
A vulnerability scanner is software that can detect vulnerabilities and weaknesses within a network, system, or application. Although the concept may seem straightforward, the process itself is more complex.
For most organisations, having a thorough understanding of assets and conducting regular vulnerability scanning is the most cost-effective approach to getting security under control.
Once vulnerabilities are detected, it's time to evaluate and assess the risk. This allows you to priortise and work on mitigation (a fancy way of saying reduce the assessed risk).
With the big budget spending around cyber security, the humble vulnerability scanner can be passed over for buzzwords like threat intelligence, red teams, security analytics, threat hunting, and even penetration testing. All these technologies and processes have their place within a security strategy, but without a clear understanding of vulnerability exposure and potential ever-expanding attack surface, these can become a distraction.
– Center for Internet Security Control 4: Continuous Vulnerability Assessment and Remediation

The Assessment Cycle
A vulnerability scanner is the tool that enables the vulnerability assessment process. There is no start and end to the security assessment process it is an ongoing effort.
Software undergoes daily discovery of new vulnerabilities, while networks constantly evolve. These two facts underscore the necessity for a continuous process essential.
Vulnerability Scanner Capabilities
Due to the broad range of vulnerabilities that need to be assessed there are a wide range of different tools to perform different types of testing.
What can a vulnerability scanner detect?
- Known Software Vulnerabilities (unpatched or unsupported software)
- Insecure Configuration within Networks and Systems (poor default security or user error)
- Default or Weak Passwords (a top access vector for attackers)
- Web Application Vulnerabilities such as SQL injection (SQLi) and Cross Site Scripting (XSS)
- Information Leaks (revealing too much configuration or other information can open doors for attackers)
With the wide range of types of vulnerabilities, there are a range of tools that can be used to detect these different vulnerability types.
Web Application Vulnerability Scanners
Web application scanning involves looking for insecure code that introduces vulnerabilities such as those from the OWASP Top 10. These vulnerabilities such as SQL Injection and Cross Site Script are not always in packaged software. Other than commercial applications these types of vulnerabilities can also be found in open source software and internally developed applications.
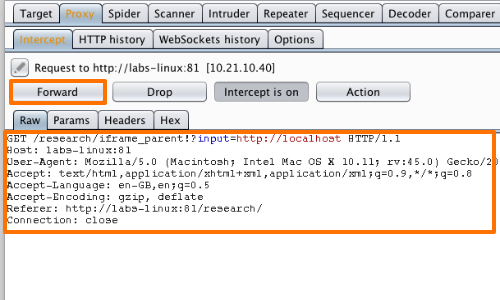
These types of scanners range from intercepting proxies such as the popular Burp Suite to the focused SQLmap a highly accurate SQL Injection testing tool. Enterprise level tools such as IBM Appscan (now known as HCL AppScan) also exist that spider an application searching for vulnerabilities. These tools are often used internally by large web application development teams as part of the secure software development life cycle (SDLC).
Network Vulnerability Scanners
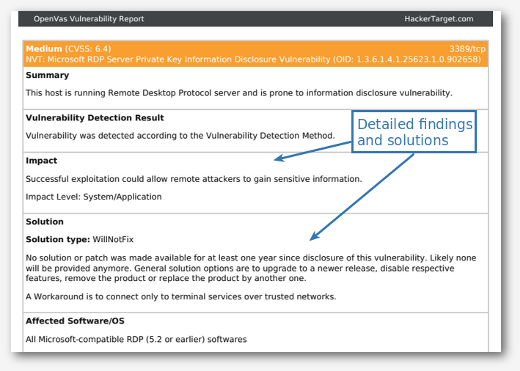
A network vulnerability scanner can go very wide but will not necessarily go deep on all vulnerability types. With these types of scanners you can have a database of over 50'000 known vulnerabilities. These will attempt to detect old server versions that have known vulnerabilities, check for default credentials and scan for known scripts. A good example of a network vulnerability scanner is the open source OpenVAS system. We use this open source tool in our suite of hosted online vulnerability scanners. Other well known examples include the commercial Nessus, and NexPose from Rapid7.
A different example of a Network Vulnerability Scanner is the Nmap Port Scanner. This tool does not go as broad in its detection, but it is more focused on mapping open ports (services) across a network. An open port that should not be accessible can still be a vulnerability.
Running a network vulnerability scanner within your network is a useful way to understand how well systems management is undertaken within the organisation. Ideally, these types of Internal scans are conducted using a credentialed scan. The scanner has valid credentials and can log onto the systems it is testing to accurately assess whether known vulnerabilities within the software and operating system have been patched.
External vulnerability scans are often conducted from outside the network perimeter and assess the external exposure of the network. That is a picture of the network from an external attacker's point of view. These types of external scans are often used to complement Internal testing. Using a different vulnerability scanner for the Internal and External scanning is generally best practice as it ensures you get the best coverage of vulnerabilities. No vulnerability scanner is perfect as it all comes down to the database of checks and the ability for the scanner to accurately match the checks with the identified attack surface.
False positives are common with most vulnerability scanners, and they can take time to confirm, but a false negative is worse. In this case, rather than detecting a vulnerability that is not present, the scanner fails to identify an actual vulnerability. By using multiple tools you are better able to avoid missing the false negative.
Attack Surface Discovery
A key to keeping your vulnerability exposure under control is to have an accurate asset register. In theory, this should detail all the endpoints, services, and web sites. However, this is rarely the case even in an organisation with a mature security practice. An attack surface discovery process emulates the attacker and can identify gaps in the asset register.
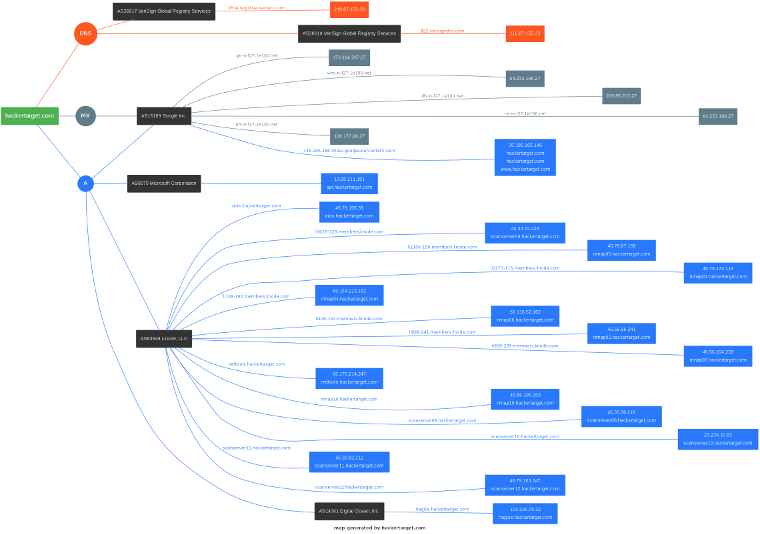
Domain Profiler Example Result
Recently several tools have become available that go deep into the process of Attack Surface Discovery.
When presented with a target organisation, an attacker will want to discover as much about the target infrastructure as possible.
Using open source intelligence resources, as well as non-intrusive or passive reconnaissance techniques the attacker can quickly identify endpoints and web sites that belong to the target.
It is then a matter of mapping the attack surface and looking for vulnerabilities. This mapping moves from passive to active discovery with packets sent to the target network. Port scanning and visiting web sites to determine web applications in use are two examples of the mapping process.
The image shows a map of a target domain that was generated using the Domain Profiler tool. It works by querying large DNS datasets and other open source information to develop an attack surface mapping of a target domain.
Focused / Specialist Scanners
Outside of the broad categories outlined above are a large number of more focused tools. A few examples of these are tools such as Nikto (web server and site scanner), WPScan (a WordPress testing tool), Aircrack-NG (wireless network testing) or one of the hundreds of tools included in the Kali Linux distribution.
Smaller, specialized tools have the advantage of probing specific vulnerability types in greater depth. They also streamline understanding of the testing process, making manual testing and verification an easier process.